

The NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) developed a cybersecurity risk framework that can be used by organizations who develop or own critical information infrastructure.
The NIST Cybersecurity Framework "focuses on using business drivers to guide cybersecurity activities and considering cybersecurity risks as part of the organization’s risk management processes. The Framework consists of three parts: the Framework Core, the Implementation Tiers, and the Framework Profiles."
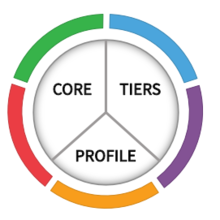
CSF Core
A taxonomy of high-level cybersecurity outcomes that can help any organization manage its cybersecurity risks.
CSF Organizational Profiles
A mechanism for describing an organization's current and/or target cybersecurity posture in terms of the CSF Core’s outcomes.
CSF Tiers
Can be applied to CSF Organizational Profiles to characterize the rigor of an organization's cybersecurity risk governance and management practices.
The NIST Cyberseucrity Framework is an implementation guide for organizations. Which brings the question: why should you as a cybersecurity professional learn about the framework? As I mentioned earlier, step one in your cybersecurity journey is to understand the industry (job market and security domains). When you embark on the learning part of your journey, you will notice that courses often have technical names (e.g., Cryptography; Digital Forensics; Penetration Testing; Security Intelligence; Web Application Security; etc.). A framework like NIST's helps you understand what is it you might be doing as a cyberseucity professional, and how your job responsibilities fit into the overall organizational objectives; and it does that in a simple non-technical language.
Framework Core
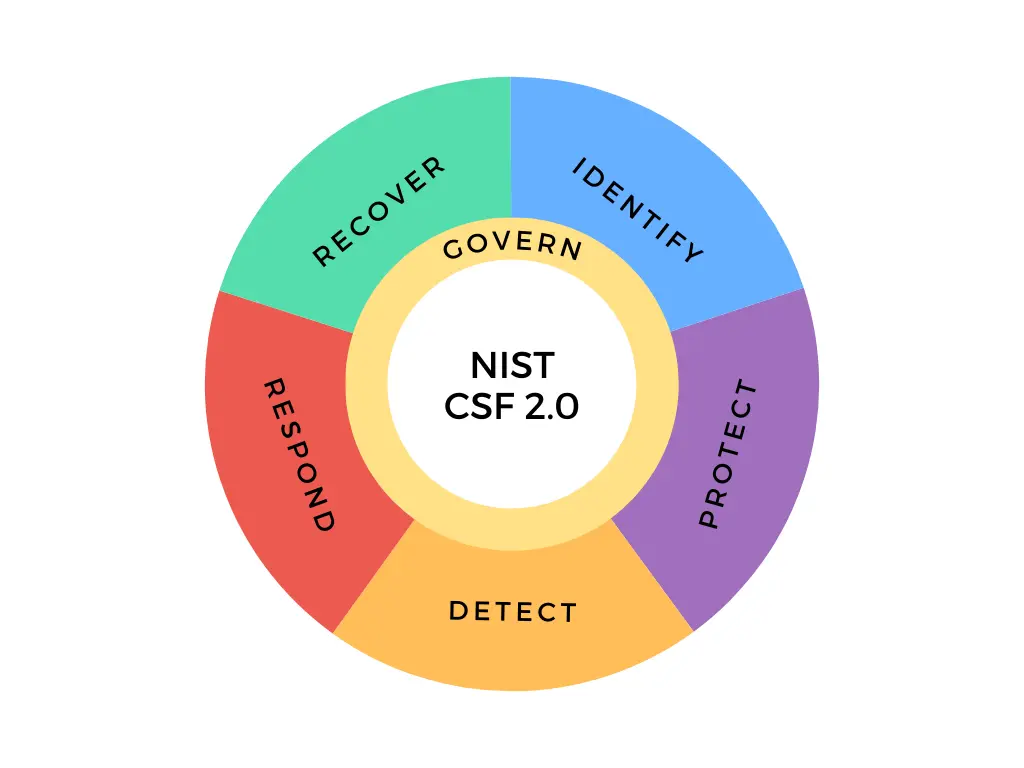
The Framework Core provides a set of activities to achieve specific cybersecurity outcomes.The Core comprises four elements: Functions, Categories, Subcategories, and Informative References. Each function within the core has categories and subcategories. There are 5 functions, 22 categories, and 97 subcategories. Subcategories are outcome-driven statements that can be used to develop a cybersecurity program.
Those pursuing a career in Cybersecurity will find it very useful to understand these core elements. As a starting point, the Core Functions represent high-level cybersecurity activities that you will be doing as a cybersecurity expert. The functions are:
The intent of this article is to introduce cybersecurity and its domains. For this reason, the Core is the main component for us. The core translates cybersecurity activities to other disciplines using simple language.
Govern (GV)
The activities in the Govern Function help establish, communicat, and monitor the organization's cybersecurity risk management strategy, expectations, and policy. Outcome Categories within this Function are:
| Organizational Context (GV.OC) | The circumstances - mission, stakeholder expectations, dependencies, and legal, regulatory, and contractual requirements - surrounding the organization's cybersecurity risk management decisions are understood. |
| Risk Management Strategy (GV.RM) | The organization's priorities, constraints, risk tolerance and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions. |
| Roles, Responsibilities, and Authorities (GV.RR) | Cybersecurity roles, responsibilities, and authorities to foster accountability, performance assessment, and continuous improvement are established and communicated. |
| Ploicy (GV.PO) | Organizational cybersecurity policy is established, communicated, and enforced. |
| Oversight (GV.OV) | Results of organization-wide cybersecurity risk management activities and performance are used to inform, improve, and adjust the risk management strategy. |
| Cybersecurity Supply Chain Risk Management (GV.SC) | Cyber supply chain risk management processes are identified, established, managed, monitored, and improved by organizational stakeholders. |
Identify (ID)
The activities in the Identify Function help organizations understand their cybersecurity risks. Outcome Categories within this Function are:
| Asset Management (ID.AM) | Assets (e.g., data, hardware, software, systems, facilities, services, people) that enable the organization to achieve business purposes are identified and managed consistent with their relative importance to organizational objectives and the organization's risk strategy. |
| Risk Management Strategy (ID.RM) | The cybersecurity risk to the organization, assets, and individuals is understood by the organization. |
| Improvement (ID.IM) | Improvements to organizational cybersecurity risk management processes, procedures and activities are identified across all CSF Functions. |
Protect (PR)
The activities in the Protect Function help develop and implement appropriate safeguards. Outcome Categories within this Function are:
| Identity Management and Access Control (PR.AC) | Access to physical and logical assets and associated facilities is limited to authorized users, processes, and devices, and is managed consistent with the assessed risk of unauthorized access to authorized activities and transactions. |
| Awareness and Training (PR.AT) | The organization’s personnel and partners are provided cybersecurity awareness education and are trained to perform their cybersecurity-related duties and responsibilities consistent with related policies, procedures, and agreements. |
| Data Security (PR.DS) | Information and records (data) are managed consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information. |
| Platform Security (PR.PS) | The hardware, software (e.g., firmware, operating systems, applications), and services of physical and virtual platforms are managed consistent with the organization's risk strategy to protect their confidentiality, integrity, and availability |
| Technology Infrastructure Resilience (PR.IR) | Security architectures are managed with the organization's risk strategy to protect asset confidentiality, integrity, and availability, and organizational resilience. |
Detect (DE)
The activities in the Detect Function help develop and implement appropriate activities to identify the occurrence of a cybersecurity event. Outcome Categories within this Function are:
| Continuous Monitoring (DE.CM) | Assets are monitored to find anomalies, indicators of compromise, and other potentially adverse events. |
| Adverse Event Analysis (DE.AE) | Anomalies, indicators of compromise, and other potentially adverse events are analyzed to characterize the events and detect cybersecurity incidents. |
Respond (RS)
The activities in the Respond Function help develop and implement appropriate activities to take action regarding a detected cybersecurity incident. Outcome Categories within this Function are:
| Incident Management (RS.MA) | Responses to detected cybersecurity incidents are managed. |
| Incident Analysis (RS.AN) | Investigations are conducted to ensure effective response and support forensics and recovery activities. |
| Incident Response Reporting and Communication (RS.CO) | Response activities are coordinated with internal and external stakeholders as required by laws, regulations, or policies. |
| Incident Mitigation (RS.MI) | Activities are performed to prevent expansion of an event and mitigate its effects. |
Recover (RC)
The activities in the Recover Function help restore assets and operations affected by a cybersecurity incident. Outcome Categories within this Function are:
| Incident Recovery Plan Execution (RC.RP) | Restoration activities are performed to ensure operational availability of systems and services affected by cybersecurity incidents. |
| Incident Recovery Communication (RC.CO) | Restoration activities are coordinated with internal and external parties. |
Implementation Tiers
Tiers represent the degree of implementation of cybersecurity risk management practices in relation to what is defined in the Framework. The Tiers range from Tier 1 to Tier 4 with an increasing degree of rigor in cybersecurity risk management implementation, based on organizational goals, rather than maturity level:
Tier 1: Partial
Tier 2: Risk Informed
Tier 3: Rpeatable
Tier 4: Adaptive
Profiles
"Profiles are an organization's unique alignment of their organizational requirements and objectives, risk appetite, and resources against the desired outcomes of the Framework Core." (NIST). Since the framework is voluntary, organizations may implement it in their own unique way. An orgnization, for instance, can develop its own current and target profiles with the goal of evaluating and ultimately improving their security posture.
#cybersecurity #nist #framework #cybersecurityframework
References
Ads by GoogleNIST NICE FrameworkThe National Initiative for Cybersecurity Education (NICE) describes the Workforce Framework for Cybersecurity (NICE Framework), a fundamental reference for describing and sharing information about cybersecurity work. The framework provides a foundation for learners including students, job seekers, and employees. The main building blocks of the NICE Framework are Tasks, Knowledge, and Skills (TKS) statements. Tasks describe the work (The "work" is what an organization needs to achieve cybersecurity risk management objectives). Knowledge and Skill statements describe the learner (The "learner" is the person who has knowledge and skills).

Tasks
A Task is an activity that is directed toward the achievement of organizational objectives. Example: Troubleshoot system hardware and software.
Knowledge
Knowledge is a retrievable set of concepts. Example: Knowledge of cyberspace threats and vulnerabilities.
Skills*
A Skill represents the capacity to perform an observable action. Example: Skill in recognizing the alerts of an Intrusion Detection System.
Competencies
Competencies provide a mechanism for organizations to assess learners. Competencies offer flexibility by allowing organizations to group together various TKS statements into an overarching category that defines a broad need.
*Ability statements from previous versions of the framework have been refactored into Skill statements#cybersecurity #careers #securityanalyst
Ads by Google