

CH2: The Web Application Security Problem
Due to the open nature of the Web, it is both a subject and an object of security breaches and attacks. This chapter outlines the inherent security problem of Web Applications. The chapter introduces Web Application security standards including the top 10 known security flaws and vulnerabilities as defined by OWASP.
Learning OutcomesLab Activity: TBA
In this practical activity, you will ...
Coming Soon »IntroductionThe Web is a vast cyberspace that is publically available and [mostly] accessible for all people anytime and from any location. Another important characteristic of the Web is the anonymity it gives for people. When we go online, we become this faceless, nameless person. This anonymity seems to give some people a pass to do things that they wouldn't otherwise.
The openness of the Web and the anonymity it provides, fosters a environment for malicious behavior. As a result, public websites present rich attack surface, but also, some websites are the object (tool) by which many attackers strike. As individuals, we are concerned about our safety and privacy, and as websites owners, we must actively protect the confidentiality, integrity, and availability of our information assets online.
A subject of attack is the target. So when a website is the subject of attack, the attacker would try to do something malicious to the website. An object of attack is the tool utilized in initiating or performing the action of the attack. When a website is the object of the attack, it sends the client malicious code.

Figure 2.1: Web Anonymity
As discussed earlier, people access websites through web browsers. The server is waiting and listening to our requests. Users' personal computers receive web pages along with related artifacts (client-side stuff). This request-response model assumes mutual trust between the participants (client and server). However, quite often, this trust is misused from both parties. An attacker can send malicious content to the server within the HTTP request. And a malicious website can send intrusive content back to us (the client) within the HTTP response.
The Inherent Problem
The inherent problem of the Web is that [web] traffic is flowing in and out between the client and the server. Ports on both sides are open and ready to accept web traffic. Therefore, security tools, like the firewall, may not protect against web attacks since they are configured to let web traffic through. On the server, for instance, ports 80 (HTTP) and 443 (HTTPS) are open otherwise the website is inaccessible (which would defeat its purpose).
Some might think that security measures taken to protect organizational infrastructure is enough to protect the web application against attacks. The reality is, web apps are attacked at the application level. In other words, attackers target the web server posing as legitimate website users.
Also, such measures as using HTTPS and Secure Socket Layer (SSL) to encrypt web traffic, only protects data while its on-the-move between the client and the server (or vice versa) but not while the data is sitting on either sides.
Implications
Security breaches in web applications may lead to serious implications. An organization's website is its public front and therefore a lot is at stake. Here are some possible implications:
References
Ads by GoogleWeb Application Security StandardsThere are few organizations that provide World Wide Web security information, guidelines, and best-practices. To name a few: OWASP, NIST, WASC, etc.
Let us start with some relevant cybersecurity definitions: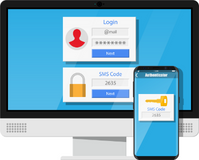
Figure 2.2: Authentication
WASC*
WASC, or the Web Application Security Consortium, is a not-for-profit charitable organization made up of an international group of experts, industry practitioners, and organizational representatives who produce open source and agreed upon best-practice security standards for the World Wide Web [3]. WASC feature articles, guidelines, and projects related Web security.
The Web Application Security Scanner Evaluation Criteria (WASSEC) is a set of guidelines to evaluate web application scanners on their ability to effectively test web applications and identify vulnerabilities. It covers areas such as crawling, parsing, session handling, testing, and reporting [3]. The course covers some of these tools.
The WASC Threat Classification (TC) clarifies and organizes the threats to the security of a web site. The aim of the project is to "develop and promote industry standard terminology for describing these issues" [3]. WASC TC provides a reference to security threats by classifying them as attacks (e.g. a brute force attack on the login page of a website), and weaknesses (e.g. server misconfiguration where the admin left few defaults unchanged).
WASC Attacks [7]WASC Weaknesses [7]NIST
The National Institute of Standards and Technology (NIST) was founded in 1901 and is now part of the U.S. Department of Commerce. The Information Technology Laboratory (ITL) is one of NIST’s six research laboratories that focuses on IT measurements, testing, and standards, and is a globally recognized and trusted source of high-quality, independent, and unbiased research and data. [5]
NIST provides information and guidelines in the form of online publications. In the are of Web Security, publication SP 800-44 provides guidelines on Securing Public Web Servers, and pubblication SP 800-95 is a guide to Secure Web Services.
OWASP
OWASP, or the Open Web Application Security Project, is a "worldwide not-for-profit charitable organization focused on improving the security of software." Their mission is "to make software security visible, so that individuals and organizations worldwide can make informed decisions about true software security risks" [6] OWASP feature many resources, guidelines, and projects related to Web security. The most relevant to this course is the OWASP Top 10 project.
"The OWASP Top Ten is a powerful awareness document for web application security. The OWASP Top Ten represents a broad consensus about what the most critical web application security flaws are" [6] Security flaws discussed in this course are based on the OWASP Top 10 project.
References
OWASP Top Ten Project
"The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications" [8].
The OWASP Top 10 Project presents a ranked list of common vulnerabilities based on severity. This ranking is not organization-specific. In the Risk Management lifecycle, Risk Assessment is the phase when we try to identify and rate threats, vulnerabilities, and risk. In other words, Risk Assessment should include vulnerability assessment. Typically, we would take vulnerability data, map it to likely threats, evaluate the severity for our environment, and articulate our own risk. For example, a very highly ranked vulnerability (e.g. Broken Access Control) might not pose a big risk for a specific organization if they have effective controls in place.

Figure 2.3: OWASP TOP 10
Common Weakness EnumerationsCWE™ is a list of software and hardware weakness types. It serves as a common language and as a baseline for weakness identification, mitigation, and prevention efforts. Each weakness has a webpage that provides detailed information including description, scope, impact, likelihood and examples. An example of a CWE weakness:
CWE-200: Exposure of Sensitive Information to an Unauthorized Actor
ID: CWE-200
Description: The product exposes sensitive information to an actor that is not explicitly authorized to have access to that information.
Alternate Terms: Information Disclosure; Information Leak
Scope: Confidentiality
Likelihood Of Exploit: High
Observed Example: CVE-2005-1205 Telnet protocol allows servers to obtain sensitive environment information from clients.
Common Vulnerabilities and ExposuresCommon Vulnerabilities and Exposures (CVE) is a public online directory that lists and defines cybersecurity vulnerabilities. There is one CVE record for each vulnerability in the catalog. The Current website is https://cve.mitre.org but a new website is underway and will be available soon (https://www.cve.org/). An example of a CVE, which is an observed example of CWE-200, is CVE-2005-1205:
CVE-2005-1205
ID: CVE-2005-1205
Descrption: The Telnet client for Microsoft Windows XP, Windows Server 2003, and Windows Services for UNIX allows remote attackers to read sensitive environment variables via the NEW-ENVIRON option with a SEND ENV_USERVAR command.
The Top 10 Web Security VulnerabilitiesThe OWASP Top 10 is not a static list. The project started in 2003 and since then there have been multiple lists, the most recent of which is the 2021 with the previous edition being the 2017. The OWASP Top Ten is developed in a hybrid manner based on data (eight of ten risks) and survey (two of ten risks). In 2017 organizations contributed data that covered over 114k applications. In 2021 the contribution more than doubled. While Data is from organizations, the Survey is from individuals. This approach allows individuals in the community identify important risks that may not be in the data from organizations.
In the 2021 Top 10 list below, you will see a reference to the 2017 list in terms of presence and position:
A01:2021-Broken Access Control moves up from the fifth position; 94% of applications were tested for some form of broken access control. The 34 Common Weakness Enumerations (CWEs) mapped to Broken Access Control had more occurrences in applications than any other category.
A02:2021-Cryptographic Failures shifts up one position to #2, previously known as Sensitive Data Exposure, which was broad symptom rather than a root cause. The renewed focus here is on failures related to cryptography which often leads to sensitive data exposure or system compromise.
A03:2021-Injection slides down to the third position. 94% of the applications were tested for some form of injection, and the 33 CWEs mapped into this category have the second most occurrences in applications. Cross-site Scripting is now part of this category in this edition.
A04:2021-Insecure Design is a new category for 2021, with a focus on risks related to design flaws. If we genuinely want to “move left” as an industry, it calls for more use of threat modeling, secure design patterns and principles, and reference architectures.
A05:2021-Security Misconfiguration moves up from #6 in the previous edition; 90% of applications were tested for some form of misconfiguration. With more shifts into highly configurable software, it’s not surprising to see this category move up. The former category for XML External Entities (XXE) is now part of this category.
A06:2021-Vulnerable and Outdated Components was previously titled Using Components with Known Vulnerabilities and is #2 in the Top 10 community survey, but also had enough data to make the Top 10 via data analysis. This category moves up from #9 in 2017 and is a known issue that we struggle to test and assess risk. It is the only category not to have any Common Vulnerability and Exposures (CVEs) mapped to the included CWEs, so a default exploit and impact weights of 5.0 are factored into their scores.
A07:2021-Identification and Authentication Failures was previously Broken Authentication and is sliding down from the second position, and now includes CWEs that are more related to identification failures. This category is still an integral part of the Top 10, but the increased availability of standardized frameworks seems to be helping.
A08:2021-Software and Data Integrity Failures is a new category for 2021, focusing on making assumptions related to software updates, critical data, and CI/CD pipelines without verifying integrity. One of the highest weighted impacts from Common Vulnerability and Exposures/Common Vulnerability Scoring System (CVE/CVSS) data mapped to the 10 CWEs in this category. Insecure Deserialization from 2017 is now a part of this larger category.
A09:2021-Security Logging and Monitoring Failures was previously Insufficient Logging & Monitoring and is added from the industry survey (#3), moving up from #10 previously. This category is expanded to include more types of failures, is challenging to test for, and isn’t well represented in the CVE/CVSS data. However, failures in this category can directly impact visibility, incident alerting, and forensics.
A10:2021-Server-Side Request Forgery is added from the Top 10 community survey (#1). The data shows a relatively low incidence rate with above average testing coverage, along with above-average ratings for Exploit and Impact potential. This category represents the scenario where the security community members are telling us this is important, even though it’s not illustrated in the data at this time.
Other OWASP ProjectsThe OWASP Foundation gives aspiring open source projects a platform to improve the security of software. Project relevant to our course:
Web Security Testing Guide
The Web Security Testing Guide (WSTG) Project is a comprehensive guide to testing the security of web applications and web services. Created by the collaborative efforts of cybersecurity professionals and dedicated volunteers, the WSTG provides a framework of best practices used by penetration testers and organizations all over the world.
OWASP Juice Shop
The OWASP Juice Shop is a sophisticated and intentionally insecure web application. Juice Shop includes vulnerabilities from the entire OWASP Top 10 along with many other security flaws found in real-world applications.
OWASP ZAP
The OWASP Zed Attack Proxy (ZAP) is a free, open-source penetration testing tool being maintained under the umbrella of the Open Web Application Security Project (OWASP). ZAP is designed specifically for testing web applications and is both flexible and extensible.
References
Chapter 2 SummaryChapter 2 Revision QuestionsAds by Google