

CH3: Identification, Authentication, and Access Control
Digital identity is the unique representation of a subject engaged in an online transaction. This chapter introduces digital identity along with its associated processes such as determining the validity of an identity claim (Authentication), and dictating who is authorized to access information resources (Access Control). This chapter explains security flaws associated with Identification, Authentication, and Access Control. Different attack vectors are presented, and prevention measures and techniques are outlined.
Learning OutcomesLab Activity: TBA
In this practical activity, you will ...
Coming Soon »Identification and AuthenticationWeb 1.0 was mainly static with public information served directly from the server's file system. Information was mostly public and serious security breaches were not a major concern. As we moved to Web 2.0 with focus on dynamic, data-driven content, the confidentiality and integrity of information emerged as a security risk. Data had to be classified (e.g., public, private, confidential) and protected with measures such as access control.
NIST Special Publication 800-63B [1] provides comprehensive guidelines for Digital Identity and Authentication. The publication defines Digital Identity as the "online persona of a subject" engaged in online transactions. This identity can be represented in several ways such as someone's email, user ID, or someone's laptop. Proving someone is who they say they are, digitally, is hard and opens opportunities for attackers to steal someone's identity.
AuthenticationDigital authentication is the "process of determining the validity of one or more authenticators used to claim a digital identity" [1]. In other words, it is the process of verifying that you are who you claim to be. In real life, in an airport, for example, your identity is verified by examining your passport information, including your photo (compared to your face). On a website, a login mechanism is used, the most common of which is the use of a username and a password.
In digital systems, such as websites, we employ credentials to perform authentication. A credential (e.g., password) binds an authenticator (e.g., a website) to the subscriber (i.e., the user), via an identifier (e.g., username or email address). Here is a question for you: do you think a password is an enough credential to protect your online identity?

Figure 3.1: Authentication (Login)
Digital authentication supports privacy protection by mitigating risks of unauthorized access to individuals’ information. The classic paradigm for authentication systems identifies three factors as the cornerstones of authentication [1]:

Figure 3.2: Securing Payments With OTP
Identification and Authentication Failures (A07:2021)
In terms of Web Security, we need to confirm the identity of a user through authentication in order to protect against authentication-related attacks. OWASP Top Ten 2021 list includes a security flaw relating to exactly that; namely, A07:2021 – Identification and Authentication Failures [2]. According to OWASP, there may be authentication weaknesses if the application:
Attack Scenario
Let's say there was a data breach on Website A and the attacker managed to get hundreds of username/password credentials. Many users reuse the same username/password combination across multiple sites:
Web Sessions
HTTP is a stateless (or connectionless) protocol in the sense that each Request-Response pair is independent, and unaware, of any other pair. But what does this really mean? Imagine you visit a website like Google and you change the default language from Arabic to English. You then save your language preference and by doing so, you send an HTTP request and receive an English homepage as a response. You then search for a term and send a new request to Google. The results come back in Arabic again (based on your location). That would be really annoying. And the reason this would happen is because the Google server doesn't know who you are and what your language preference is; it simply "forgot" you.
The fact that HTTP is stateless poses a real problem. It makes the Web as we know it, impossible. No client would be able to maintain a continuous "conversation" with the server. Luckily, the solution is available in the form of the SESSION object. The session is the mechanism by which the client and the server can establish a conversation.
So how does the session work? Let's use the same Google example. You visit Google for the first time from Dubai and you get the homepage in Arabic. You change the preference and send it via an HTTP request. The server responds but this time, it sends you a unique identifier called the SESSION TOKEN along with the response. Next, you search for something, but this time you include the session token with the new request. The server recognizes this token and associate it with you and your preferences.
Session Management
Because of its importance, the Session must be handled and managed very carefully. The session is not only used to save user preferences, it is also often used in tandem with authentication and access control. Session Management involves:
Attack Scenario
Let's say someone accessed their online banking website from a public computer (not a good idea to start with):
Prevention Measures
In order to prevent Identification and Authentication failures, measures can be taken in two main areas:
References
Access ControlAccess control (or Authorization) is a fundamental information security component that dictates who is authorized to access information resources. Information Security involves the protection of information and its critical elements, including systems and hardware that use, store, and transmit that information. The golden standard for Information Security is based on protecting the C.I.A triad of information.
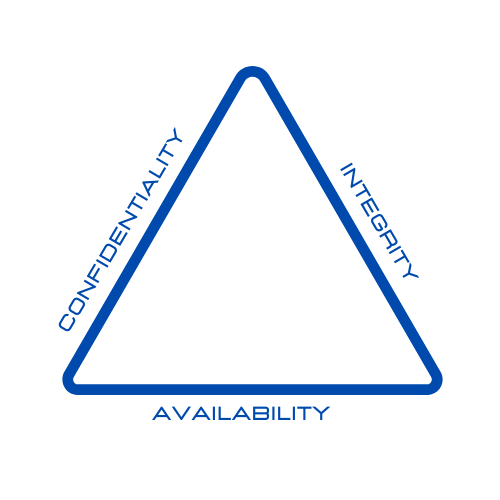
Figure 3.3: The C.I.A Triad
A breach in Confidentiality means unauthorized people can view information they should not be able to view. Imagine a patient is able to see not only their medical records but also the records of other patients. A breach in Integrity, on the other hand, means unauthorized people can change information they should not be able to modify. Should an online shopper be able to change the price of an item before they buy it? Of course, NOT!
Access control should regulate:
Access control dictates that users cannot act outside of their intended permissions. In other words, they cannot view, modify, or delete information without permission. Broken Access Control is a failure to implement or enforce access control measures.
Broken Access Control (A01:2021)When Access Control fails, hackers may be able to gain access to confidential resources including the ability to make unauthorized modifications to breach resources. In Web applications, this may have devastating impact; a hacker may bypass the authentication mechanism (i.e., login) and gain access to restricted areas of the website. Let's consider the following scenario:
Attack Scenario
Once logged in, the URL of the customer's dashboard webpage for Insecure Bank looks like this:
https://insecurebank.ae/customer?id=1234
Notice the URL parameter named id with a value equals to 1234. If no additional access control measures are in place, any user can modify the value, say from id=1234 to id=5678, and potentially access another customer's dashboard. In this scenario, the only access control measure would've been the login authentication using the customer's credenitals (username and password).
The main security flaw in this website is Broken Access Control. The attacker in this case, however, exploited a specific vulnerability; namely bypassing access control via parameter tampering (aka, force browsing). This, in turn, implies that there may be a number of vulnerabilities that can lead to a breach (e.g., missing access controls for unsafe HTTP methods such as POST, PUT and DELETE).
Prevention Measures
One way to prevent breaches due to Broken Access Control is to fix all possible vulnerabilities (see OWASP list here »). But what if there are zero-day vulnerabilities? A much better approach is to design access control from the start. Security should be part of the Software Development Lifecycle (SDLC), rather than an after thought. The following are Access Control design principles that must be considered at early stages of web application development:
if user.role=="teacher"
Grade.Change
Code 3.1: Hard-Coded Role Rule
if user.hasaccess=="Grade_Change"
Grade.Change
Code 3.2: Attribute-Based RuleReferences
Ads by GoogleChapter 3 SummaryChapter 3 Revision QuestionsAds by Google