

Module 1: Introduction to Network SecurityNetwork Security Samer Aoudi
Learning Outcomes1.1. Intro to Computer NetworksNetwork security is a critical aspect of protecting an organization's information systems and assets. With the increasing reliance on technology, networks have become a primary target for cybercriminals and malicious actors. These actors seek to exploit vulnerabilities in networks to gain unauthorized access, steal sensitive information, or disrupt operations. Network security involves implementing a variety of controls, such as firewalls, intrusion detection systems, and encryption, to prevent unauthorized access and protect against a wide range of cyber threats. This chapter will provide an overview of the key concepts and principles of network security, including the types of threats that organizations face, the vulnerabilities that can be exploited, and the controls that can be implemented to protect against these threats.
1.1.1. Computer Networking Fundamentals
A computer network is a collection of interconnected devices, such as computers, servers, printers, and routers, that are connected together to share resources and exchange information. These devices communicate with each other using a variety of protocols and technologies.
Types of Networks
Networks can be categorized based on several factors, such as their size, architecture, topology, and communication protocols. The specific categorization of a network may depend on the context in which it is being used, as well as the needs and requirements of the users. Here are some common network types:
Network Topologies
A network topology refers to the physical or logical arrangement of devices, nodes, and connections in a computer network. In simpler terms, it describes the way in which nodes or devices are connected to each other and how data flows between them. There are several types of network topologies, including:
The OSI Reference Model
The OSI (Open Systems Interconnection) reference model is a framework for understanding how data is transmitted over a network. It defines a layered architecture that separates the functions of a network into seven different layers, each of which is responsible for a specific set of tasks. The OSI model is a logical model and does not specify any particular protocol, it is used as a reference model to understand the different layers of network protocols and how they work together.
The seven layers of the OSI model are shown in the table below [1]:
| Layer | Function |
|---|---|
| Physical Layer | Responsible for transmitting raw data bits over a physical medium such as a cable |
| Data Link Layer | Responsible for providing reliable communication between devices on the same local network |
| Network Layer | Responsible for routing data packets to their destination |
| Transport Layer | Responsible for ensuring reliable end-to-end communication between devices |
| Session Layer | Responsible for establishing, maintaining, and terminating sessions between applications |
| Presentation Layer | Responsible for translating data into a format that can be understood by the application layer |
| Application Layer | Responsible for providing the interface between the network and the end-user applications. |
Table 1.1: OSI Layers
The OSI model provides a common framework that allows network professionals to understand how different networking technologies and protocols work together to transmit data over a network. It also helps in troubleshooting network issues by identifying and isolating problems at the appropriate layer.
The TCP/IP Stack
TCP/IP (Transmission Control Protocol/Internet Protocol) is a set of networking protocols that are used to transmit data over networks, particularly the internet. It is the foundation of most modern networks, including the internet and most local area networks (LANs). The TCP/IP stack is the combination of several protocols that work together to transmit data over a network.
The TCP/IP stack is made up of four layers shown in the figure below [2]:
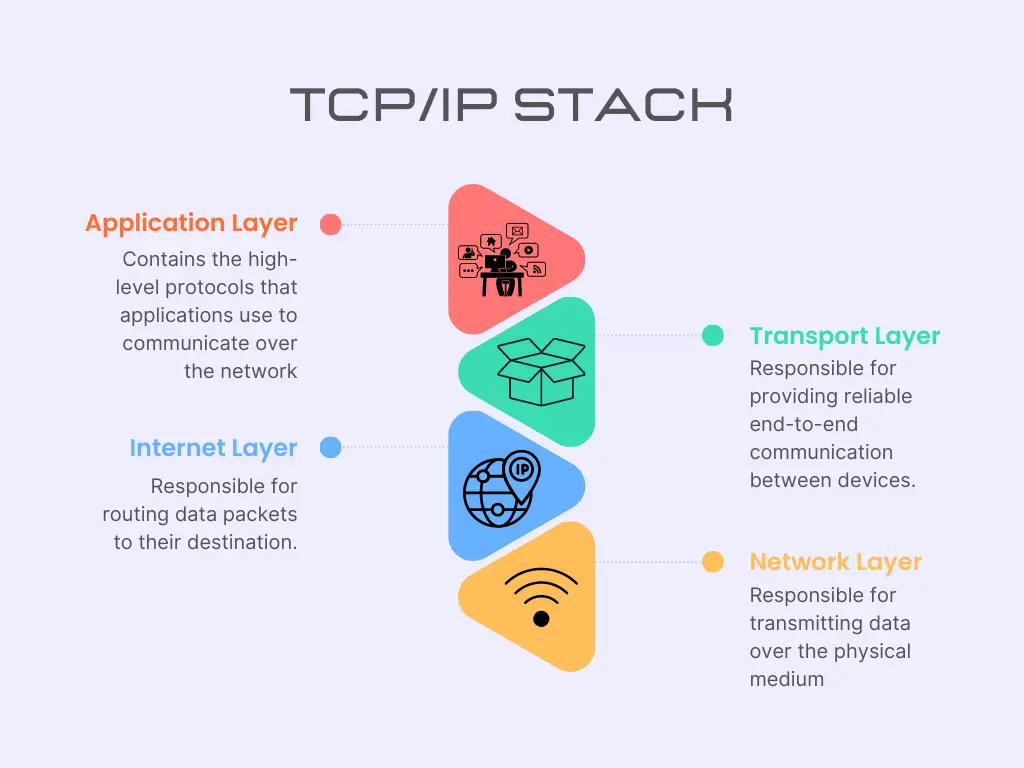
Figure 1.1: TCP/IP Stack Layers
The TCP/IP stack layers and functions are shown in the table below [2]:
| Layer | Function |
|---|---|
| Network Access Layer | Responsible for transmitting data over the physical medium. It includes protocols such as ARP (Address Resolution Protocol) and ICMP (Internet Control Message Protocol) |
| Internet Layer | Responsible for routing data packets to their destination. It includes the IP (Internet Protocol) protocol, which is responsible for addressing and routing packets |
| Transport Layer | Responsible for providing reliable end-to-end communication between devices. It includes the TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) protocols |
| Application Layer | Contains the high-level protocols that applications use to communicate over the network. Examples include HTTP (Hypertext Transfer Protocol), FTP (File Transfer Protocol), and DNS (Domain Name System) |
Table 1.2: TCP/IP Layers
The TCP/IP stack is designed to be a robust and flexible set of protocols that allow different types of devices to communicate with each other regardless of the underlying hardware or software. The protocols in the stack work together to ensure that data is transmitted reliably and efficiently over the network.
The OSI reference model and the TCP/IP stack are both frameworks for understanding how data is transmitted over a network. However, they have some important differences.
The OSI model is a logical model that defines a layered architecture that separates the functions of a network into seven different layers, each of which is responsible for a specific set of tasks. It is a framework for understanding how different networking technologies and protocols work together to transmit data over a network. It does not specify any particular protocol, but it is used as a reference model to understand the different layers of network protocols and how they work together.
The TCP/IP stack, on the other hand, is a set of specific protocols that are used to transmit data over the internet and most local area networks (LANs). It is made up of four layers: the Application, Transport, Internet, and Network Access layers. Each layer has its specific function and protocols to work with.
Simply put, the OSI model is a general model that can be applied to any network communication, while the TCP/IP stack is specifically designed for the internet and most LANs.
Network Devices
There are several common network hardware devices that are used in modern computer networks. Some of the most common network hardware devices include:

Figure 1.2: Network Devices
1.1.2. Network Protocols
A network protocol is a set of rules and standards that govern the communication between devices in a computer network. It defines how data is transmitted, formatted, and processed between devices, and establishes a common language that allows devices from different manufacturers or operating systems to communicate with each other. Network protocols are responsible for ensuring that data is transmitted reliably and efficiently, and they provide mechanisms for error detection and correction.
DNS
The Domain Name System (DNS), a critical component of the internet infrastructure, is a distributed naming system used to translate human-readable domain names (such as www.sameraoudi.com) into IP addresses (such as 192.0.2.1) that computers use to identify each other on a network. DNS allows users to access websites and other network resources by typing a domain name into a web browser or other application, rather than having to remember the IP address of the resource they want to access. DNS servers are responsible for storing and managing information about domain names and their corresponding IP addresses.
When a user enters a domain name into their browser, the browser sends a DNS query to a DNS server to look up the IP address associated with that domain name. If the DNS server has a record of the domain name and its associated IP address, it returns the IP address to the browser, which then uses it to connect to the desired resource.
ARP
Address Resolution Protocol (ARP) is a network protocol used to map a network address (such as an IP address) to a physical address (such as a MAC address) in a local area network (LAN). When a device needs to communicate with another device on a LAN, it uses ARP to determine the physical address of the device it wants to communicate with. The device sends out an ARP request containing the IP address of the target device, and the target device responds with its MAC address. Once the requesting device has obtained the MAC address of the target device, it can use that address to communicate with the target device directly over the LAN. ARP operates at the Data Link Layer of the OSI network model.
ARP is critical for enabling devices on a LAN to communicate with each other effectively. Without ARP, devices would have to rely solely on IP addresses to communicate with each other, which can be less efficient and less reliable than using physical addresses.
DHCP
Dynamic Host Configuration Protocol (DHCP) is a network protocol that is used to automatically assign IP addresses and other network configuration information to devices on a network. DHCP servers are responsible for managing the allocation of IP addresses to devices on a network. When a device connects to a network, it sends out a DHCP request to the DHCP server, requesting an IP address and other network configuration information. The DHCP server then assigns an available IP address to the device and provides it with the necessary network configuration information, such as the subnet mask, default gateway, and DNS server addresses.
DHCP allows network administrators to easily manage and maintain the IP addresses and other network configuration information for devices on a network. By using DHCP, administrators can ensure that devices are assigned unique IP addresses and that network configuration information is automatically provided to them.
DHCP is widely used in local area networks (LANs) and is an essential component of modern network infrastructure. It simplifies the process of network configuration and management, making it easier for organizations to deploy and maintain large-scale networks.
IP
Internet Protocol (IP) is a network protocol that is used to route data packets between devices on the Internet or other computer networks. IP provides a standardized method for addressing and routing data packets between devices on a network. Each device on a network is assigned a unique IP address, which is used to identify the device and route data packets to it. IP addresses are typically represented as a series of four numbers separated by dots (e.g., 192.0.2.1).
IP operates at the Network Layer of the OSI network model and is responsible for routing data packets between devices on a network. It works in conjunction with other network protocols, such as TCP (Transmission Control Protocol) and UDP (User Datagram Protocol), to provide reliable and efficient data transfer over a network.
IP is a fundamental component of the Internet and is used by billions of devices to communicate with each other every day. It allows devices on different networks to communicate with each other seamlessly and efficiently, enabling the modern connected world we live in today.
IP Classes
IPv4 network addresses are divided into five classes, namely A, B, C, D, and E. These classes are defined based on the number of bits used for the network and host addresses in the IP address. The five IPv4 classes are:
ICMP
Internet Control Message Protocol (ICMP) is a network protocol that is used to send error messages and operational information about network conditions between devices on the Internet or other computer networks. ICMP is used by network devices, such as routers and firewalls, to communicate with each other and to detect and diagnose network problems. It can be used to check the availability of a network host, measure network latency, and diagnose network connectivity problems.
ICMP messages are typically generated automatically by network devices in response to certain events, such as a packet being dropped or a network device becoming unavailable. They are then sent to the source device to inform it of the problem or to request additional information.
Some common uses of ICMP include the "ping" command, which sends an ICMP echo request to a network host to check its availability, and the "traceroute" command, which uses ICMP to measure network latency by sending packets with increasing time-to-live (TTL) values and measuring the response times.
ICMP is an essential component of modern network infrastructure and is used by virtually every device on the Internet to communicate with other devices and to diagnose network problems.
IGMP
Internet Group Management Protocol (IGMP) is a network protocol used to manage IP multicast groups in a network. Multicast is a method of transmitting data to multiple devices simultaneously. In a multicast transmission, a single packet is sent from the source device and is received by all devices in the multicast group. This is in contrast to unicast, where a separate packet is sent to each individual device, and broadcast, where a packet is sent to all devices on a network.
IGMP is used by devices to join or leave multicast groups and to communicate with other devices in the group. When a device wants to join a multicast group, it sends an IGMP join message to the local multicast router. The router then adds the device to the multicast group and begins forwarding multicast packets to it. When a device wants to leave a multicast group, it sends an IGMP leave message to the router, which then removes the device from the group.
IGMP operates at the Network Layer of the OSI network model and is an essential component of modern network infrastructure. It allows devices to efficiently receive multicast data and enables applications such as streaming video and audio over a network.
Computer networking is the foundation that enables the communication and exchange of data between different devices and systems. It allows devices to connect and share resources, access the internet, and exchange information. This makes network security an essential aspect of protecting an organization's information and systems.
References
1.2. Network Security
Network security refers to the measures and practices designed to protect computer networks from unauthorized access, misuse, modification, or destruction. The main goal of network security is to ensure the confidentiality, integrity, and availability of the network and the data it contains.
Network security can be achieved through a combination of technologies, policies, and procedures, including firewalls, access control, encryption, awareness training, and so on. Network security is an ongoing process that requires regular monitoring, testing, and updating. Network administrators must stay up-to-date with the latest security threats and implement appropriate measures to mitigate them.
1.2.1. Threats to Network Security
In modern computing, networks have become a crucial component in connecting individuals, organizations, and devices worldwide. Networks are built on a layered architecture that facilitates efficient communication between various devices and systems. However, each layer in the network architecture is susceptible to various types of security threats that can compromise the confidentiality, integrity, and availability of data transmitted over the network. Understanding the different layers in the network architecture and the corresponding security threats is essential to ensure that networks are protected from unauthorized access, malicious attacks, and other potential security breaches.
However, before we discuss threats to network security, let us differentiate between Active and Passive attacks:
A passive attack is an attempt by an unauthorized person or system to intercept and read sensitive data without modifying it. Passive attacks include activities such as eavesdropping, sniffing, and data interception. These attacks do not alter or modify the information being transmitted, but rather seek to obtain information that is being transmitted in plain text or otherwise unencrypted.
An active attack on the other hand, is an attempt to modify or tamper with data, disrupt network operations, or steal information. Active attacks are more dangerous than passive attacks because they can alter or destroy data, making it more difficult to detect and recover from. Examples of active attacks include malware, viruses, denial-of-service (DoS) attacks, and man-in-the-middle (MitM) attacks.
Application layer Threats
The Application layer of the TCP/IP stack is where most security threats occur, as it is the layer where user interactions and access to data takes place. The following are some common security threats that can occur at the Application layer:
Transport layer Threats
The Transport layer of the TCP/IP stack is responsible for providing reliable end-to-end communication between devices. The main security threats at this layer are:
Internet layer Threats
The Internet layer of the TCP/IP stack is responsible for routing data packets to their destination. The main security threats at this layer are:
Network Access layer Threats
The Network Access layer of the TCP/IP stack is responsible for transmitting data over the physical medium. The main security threats at this layer are:
1.2.2. Network Security Components
As mentioned above, network security can be achieved through a combination of technologies, policies, and procedures working together to identify, detect, protect, respond, and recover in the event of a security incident. Effective network security requires a comprehensive approach that addresses multiple components and adapts to the changing threat landscape.
Defense in depth, for instance, is a security strategy that involves deploying multiple layers of security controls to protect against a variety of security threats. The goal of defense in depth is to provide redundancy and diversity in security measures so that if one layer of defense is breached, there are other layers in place to prevent or mitigate the impact of the breach.
Each layer of defense in depth provides a unique type of protection and may include different security controls such as firewalls, intrusion detection and prevention systems, access control, encryption, and physical security measures.
The components of a defense in depth strategy typically include: When applying a defense in depth strategy, the following components, or layers, are commonly implemented:
In addition to the above layers, the following components are commonly utilized:
Network Perimeter Security
Network perimeter security refers to the set of security measures that are implemented at the boundary of a network to protect it from unauthorized access and threats from external sources. The network perimeter is the first line of defense against cyber threats and is typically guarded by firewalls, intrusion detection and prevention systems (IDPS), and virtual private networks (VPNs).
Identity and Access Management (IAM)
Identity and Access Management (IAM) is a security framework that governs and manages user access to network resources. IAM aims to ensure that only authorized individuals have access to specific resources and that their access is limited to what they require to perform their job functions.
IAM is typically achieved through a combination of policies, procedures, and technology. It involves managing user identities, authentication, and access control to network resources through various means such as passwords, tokens, biometrics, and certificates.
Contingency Planning
Contingency planning in the context of network security refers to the process of creating a set of procedures and policies to ensure that an organization can continue to operate its network and IT systems in the event of a disruption or disaster. The goal of contingency planning is to minimize the impact of a disruption on an organization's network and to enable the organization to recover quickly and efficiently.
Contingency planning typically involves identifying potential risks and threats to an organization's network, and developing plans to address those risks. For example, an organization may develop a contingency plan for a natural disaster such as a hurricane, by creating procedures for shutting down and securing its network and IT systems in advance of the storm, and for restoring operations once the storm has passed.
Contingency planning also includes creating backup systems and data recovery plans to ensure that critical data and systems can be recovered in the event of a disruption. This may involve backing up data to off-site locations, or creating redundant systems and networks to ensure that critical systems and services remain available during a disruption.
Incident response involves the process of identifying, assessing, and responding to security incidents or cyber attacks that threaten an organization's information systems, data, or network. The goal of incident response is to minimize the impact of a security breach by quickly containing and mitigating the incident, restoring normal operations, and preventing similar incidents from occurring in the future. An effective incident response plan should include procedures for detecting and reporting incidents, evaluating the scope and severity of the incident, containing the incident, and analyzing the incident to prevent future occurrences.
Disaster recovery is a process for restoring IT infrastructure, data, and systems to their normal operations after a catastrophic event such as a natural disaster, cyber attack, or other disruptive event that impacts an organization's ability to operate. Disaster recovery planning involves creating backup systems, data replication, and other measures to ensure that critical data and systems can be recovered in the event of a disaster. The goal of disaster recovery is to minimize the downtime and data loss caused by a disaster and to restore normal operations as quickly as possible.
1.2.3. Network Security Technologies
Network security technologies play a crucial role in protecting networks from a wide range of security threats. These technologies can be used to secure network devices, encrypt data, and monitor network activity to detect and prevent unauthorized access. In this section, we will provide an overview of the most important network security technologies, including firewalls, intrusion detection and prevention systems, VPNs, and encryption. We will explain how these technologies work and their specific use cases to help you understand how to use them to protect your network. Additionally, we will discuss the advantages and disadvantages of each technology, and how to properly implement them for maximum security.
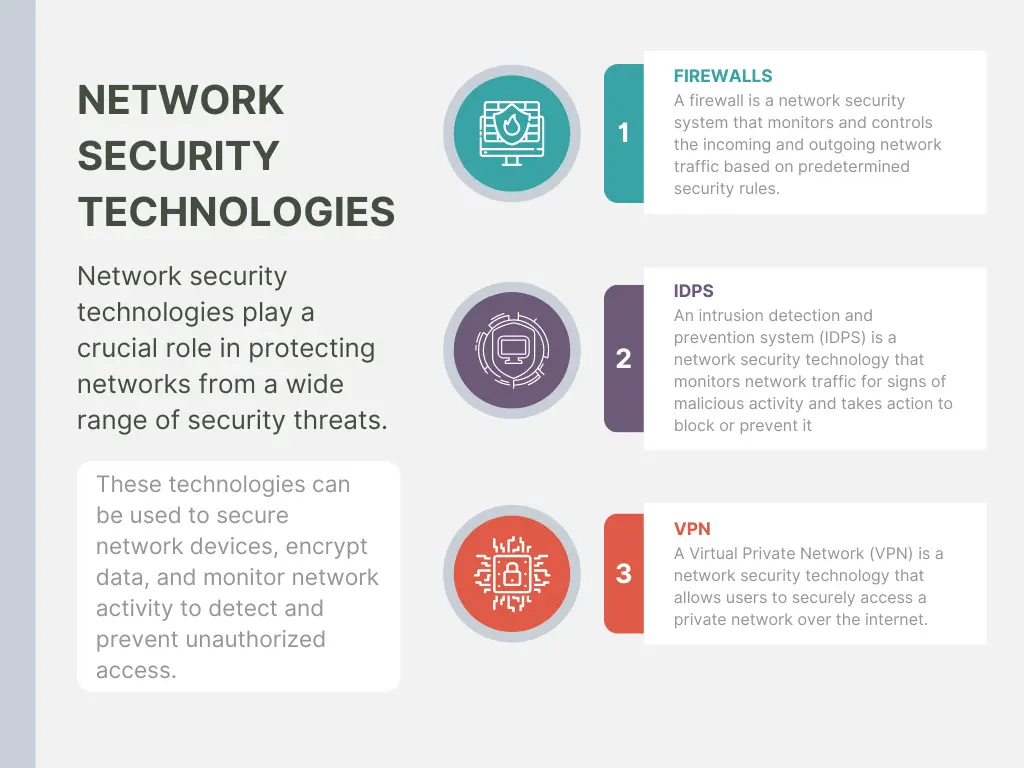
Figure 1.3: Network Security Technologies
Firewalls
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls are typically implemented as a software or hardware solution, and they can be placed at various points in a network to protect it from unauthorized access.
Firewalls use a set of predefined security rules, also called access control lists (ACLs) or policies, to determine which traffic is allowed to pass through and which traffic should be blocked. These rules are based on various parameters such as IP addresses, ports, and protocol. For example, a firewall can be configured to block all incoming traffic from a specific IP address or to only allow traffic over a specific port.
It is important to note that there are several types of firewalls, including:
Firewalls are considered to be an essential component of network security and are widely used to protect both internal and external networks. They are able to block unauthorized access and prevent sensitive data from being stolen or modified. However, firewalls are not a one-stop solution for network security, and it's important to use them in conjunction with other security technologies and best practices for optimal protection.
Intrusion Detection and Prevention Systems (IDPS)
An intrusion detection and prevention system (IDPS) is a network security technology that monitors network traffic for signs of malicious activity and takes action to block or prevent it. IDPS can be implemented as a software or hardware solution, and it can be placed at various points in a network to protect it from unauthorized access.
An IDPS is designed to detect and prevent a wide range of security threats, such as malware, DDoS attacks, and unauthorized access attempts. It does so by analyzing network traffic in real-time, looking for patterns and anomalies that may indicate a security threat. Once a threat has been detected, the IDPS can take action to block the traffic or alert a security administrator.
There are two main types of detection in IDPS:
There are two main types of IDPS: Network Intrusion Detection Systems (NIDS) and Host-based Intrusion Detection Systems (HIDS)
Both NIDS and HIDS have their own advantages, NIDS are better suited to detect network-wide attacks while HIDS are better at detecting targeted attacks on a specific host.
Virtual Private Network (VPN)
A Virtual Private Network (VPN) is a network security technology that allows users to securely access a private network over the internet. VPNs use encryption and authentication to protect the privacy and security of data as it travels over the internet. They are widely used by organizations to protect remote access to their internal networks, and also by individual users to protect their internet browsing activity.
VPNs work by creating a secure and encrypted "tunnel" between the user's device and the VPN server, which enables secure and private communication over the internet. This is achieved by using a combination of protocols and encryption standards, such as Internet Protocol Security (IPsec), Secure Sockets Layer (SSL) and Transport Layer Security (TLS).
VPNs can be used in conjunction with other network security technologies such as firewalls and intrusion detection and prevention systems (IDPS) to protect both internal and external networks. For example, a firewall can be used to block unauthorized access to the internal network, while a VPN can be used to securely allow remote access to the internal network.
Network security technologies such as firewalls, intrusion detection and prevention systems (IDPS), Virtual Private Networks (VPNs) and encryption play a crucial role in protecting networks from various security threats. However, it's important to remember that these technologies are not a one-stop solution for network security and should be used in conjunction with other security technologies and best practices for optimal protection.
Case StudyInvestigating the Effectiveness of Firewalls in Protecting Corporate NetworksBackground
In today's digital age, corporations rely heavily on technology to conduct their business operations. As a result, corporate networks have become a prime target for cyber attacks. One common defense against these attacks is the use of firewalls. Firewalls are designed to block unauthorized access to a network and to protect against malicious activity. However, the effectiveness of firewalls in protecting corporate networks is not well understood.
Case Study
CSF Corporation is a large retail company with a significant online presence. The company's network infrastructure includes a firewall to protect against cyber attacks. In recent months, the company has experienced a number of security breaches, raising concerns about the effectiveness of the firewall in protecting the network.
Methods
In order to investigate the effectiveness of the firewall in protecting the corporate network, the following methods were used:
Results
The network analysis revealed that there were several vulnerabilities in the network infrastructure that could have allowed the security breaches to occur. The firewall configuration review found that the firewall was not properly configured and that several important security measures were not in place. The penetration testing revealed that the firewall was not able to block all unauthorized access to the network. The log analysis showed that there were several attempts to bypass the firewall.
Conclusion
The results of this case study indicate that the firewall was not effective in protecting the corporate network of XYZ Corporation. The vulnerabilities in the network infrastructure, improper firewall configuration, and the ability of attackers to bypass the firewall all contributed to the security breaches experienced by the company. Based on these findings, it is recommended that XYZ Corporation takes steps to address these issues and to improve the overall security of their network. This may include implementing more robust security measures, regular security assessments, and employee security training.
Case Study Questions
Attempt to answer the following questions before revealing the model answers:
This case study highlights the importance of regularly assessing and maintaining network security measures, such as firewalls. It also illustrates the complexity of securing corporate networks and the need for organizations to take a comprehensive approach to security. The findings of this case study can serve as a valuable lesson for other organizations looking to improve their network security and protect against cyber attacks.
Research AssignmentInvestigating the Effectiveness of Network Intrusion Detection Systems in Detecting and Responding to Advanced Persistent ThreatsObjective
The goal of this research project is to evaluate the effectiveness of network intrusion detection systems (NIDS) in detecting and responding to advanced persistent threats (APTs).
Background
With the increasing reliance on technology and the internet in various industries, the threat of cyber attacks has become a major concern for organizations. Advanced persistent threats (APTs) are a particularly significant concern as they are typically carried out by highly skilled and well-funded attackers who are able to evade traditional security measures. One potential defense against APTs is the use of network intrusion detection systems (NIDS), which are designed to detect and respond to malicious activity on a network. However, the effectiveness of NIDS in detecting and responding to APTs is not well understood.
Method
In order to evaluate the effectiveness of NIDS in detecting and responding to APTs, the following methods will be used:
Expected Results
The results of this research project will provide insight into the effectiveness of NIDS in detecting and responding to APTs. It is expected that the results will identify areas where NIDS can be improved to better detect and respond to APTs, as well as areas where additional research is needed.
Assessment Criteria
The results of this research will have important implications for organizations that rely on technology and the internet to conduct their business. By providing a better understanding of the effectiveness of NIDS in detecting and responding to APTs, this research will help organizations to better protect themselves against these types of attacks. Additionally, the results of this research may also inform future developments in the field of network security.
Ads By Google
Module SummaryModule Revision QuestionsModule Glossary| Term | Definition |
|---|---|
| LAN | A Local Area Network (LAN) is a network that connects devices within a limited area, such as an office |
| WAN | A Wide Area Network (WAN) is a network that connects devices over a large geographic area |
| MAN | A Metropolitan Area Network (MAN) is a network that covers a larger area than a LAN but smaller than a WAN |
| WLAN | A Wireless Local Area Network (WLAN) is a wireless network that uses radio waves to connect devices |
| PAN | A Personal Area Network (PAN) is a network that connects devices within a personal space |
| CAN | A Campus Area Network (CAN) is a network that connects multiple LANs within a campus or university |
| SAN | A Storage Area Network (SAN) is a network that provides block-level access to storage devices |
| VPN | A Virtual Private Network (VPN) is a secure network that allows users to access a private network, such as a corporate network |
| P2P | A Peer-to-peer Network (P2P) is a decentralized network in which devices connect directly to each other to share resources |
| OSI | The Open Systems Interconnection (OSI) reference model is a framework for understanding how data is transmitted over a network |
| TCP/IP | Transmission Control Protocol/Internet Protocol is a set of networking protocols that are used to transmit data over networks, particularly the internet |
| NIC | A Network Interface Card (NIC) is a hardware component that enables a computer to connect to a network |
| DNS | Domain Name System (DNS) is a distributed naming system used to translate human-readable domain names |
| ARP | Address Resolution Protocol (ARP) is a network protocol used to map a network address |
| DHCP | Dynamic Host Configuration Protocol (DHCP) is a network protocol that is used to automatically assign IP addresses |
| ICMP | Internet Control Message Protocol (ICMP) is a network protocol that is used to send operational information about network conditions |
| IGMP | Internet Group Management Protocol (IGMP) is a network protocol used to manage IP multicast groups |
| IAM | Identity and Access Management (IAM) is a security framework that governs and manages user access to network resources |
| IDPS | Intrusion Detection And Prevention Systems (IDPS) is a network security technology that monitors network traffic for signs of malicious activity and takes action to block or prevent it |
| NIDS | A Network Intrusion Detection System (NIDS) monitors network traffic for signs of malicious activity and takes action to block or prevent it |
| HIDS | A Host-based Intrusion Detection System (HIDS) runs on individual hosts or devices and monitors the system activity and configuration for signs of malicious activity |