

Module 5: Implementing Network SecurityNetwork Security Samer Aoudi
Learning Outcomes5.1. Mitigating Network Attacks
In today's interconnected world, network security has become an essential requirement for businesses, organizations, and individuals. Network security implementation refers to the process of securing a computer network from unauthorized access, misuse, modification, or destruction of data. The goal of network security is to protect the confidentiality, integrity, and availability of information and network resources. Network security implementation involves the use of various technologies, policies, and procedures to ensure that the network and the data transmitted over it are safe from external and internal threats. In this rapidly evolving digital landscape, implementing effective network security measures has become more critical than ever to safeguard against cyber threats, data breaches, and other malicious activities.
5.1.1. An Overview of Network Architecture
Network architecture refers to the design and structure of a computer network, including its physical and logical layout, protocols, and communication technologies. It involves planning and organizing the various components of a network, such as routers, switches, servers, and cabling, to ensure that data can be transmitted reliably and efficiently between devices.
switched network
A switched network is a type of computer network architecture in which devices are connected to a central switching device, such as a switch or a router, that facilitates communication between the devices. In a switched network, each device is connected to a port on the switch, and the switch uses its internal logic to route traffic between the devices.
Compared to older network architectures, such as hub-based networks, switched networks offer several advantages, including:
Virtual Local Area Network (VLAN)
A Virtual Local Area Network (VLAN) is a logical network that is created by grouping together devices on a physical network, even if they are not located in the same physical location. A VLAN can span across multiple switches, routers, or other network devices, and can be used to segment a network into multiple broadcast domains, isolate traffic, and improve network performance and security.
In a VLAN, devices that are members of the same VLAN can communicate with each other as if they were on the same physical network, even if they are physically separated by other devices that are not part of the VLAN. VLANs are typically created and managed using software-based tools, such as a network management system or switch management interface.
Each VLAN is identified by a unique VLAN ID (VID), which is a number between 1 and 4094. Switches and routers can use the VLAN ID to differentiate between VLANs and forward traffic between them. VLANs can also be associated with specific ports on a switch, so that any device connected to that port is automatically added to the associated VLAN.
VLANs offer several benefits, including improved network security, better network performance, and greater flexibility in network design. By segmenting a network into multiple VLANs, organizations can isolate sensitive traffic, such as financial data or customer information, from other parts of the network. VLANs can also improve network performance by reducing broadcast traffic and enabling more efficient use of bandwidth. Finally, VLANs can enable organizations to easily create and manage multiple logical networks within a single physical network infrastructure.
5.1.2. Common Network Attacks and Countermeasures
All layers of TCP/IP have their own security threats and vulnerabilities. When a lower layer is hacked, communications are compromised without the other layers being aware of the problem. Everything at Layer 3 (Network) and higher is encapsulated into some type of Layer 2 (Data Link) frame. If an attacker can interrupt, copy, redirect, or confuse the Layer 2 forwarding, they can also disrupt the functions of the upper-layer protocols.
Sniffing
Sniffing is the act of intercepting and capturing network traffic as it passes between devices on a network. This can be done using specialized software or hardware tools known as network sniffers or packet analyzers.
Sniffing is often used by network administrators to troubleshoot network problems and diagnose performance issues. However, it can also be used by attackers to eavesdrop on network traffic and steal sensitive information, such as usernames and passwords, credit card numbers, and other confidential data.
Sniffing can be carried out using various techniques, including:
To prevent sniffing attacks, several countermeasures can be implemented, including:
DHCP server spoofing
DHCP server spoofing is a type of network attack in which an attacker sets up a rogue DHCP server on a network in order to intercept and redirect network traffic. The attacker typically uses the rogue server to assign IP addresses to devices on the network, and can also configure the server to provide fake DNS and gateway information to the devices.
This type of attack can be used to redirect network traffic to malicious servers, steal sensitive information, or launch other types of attacks, such as man-in-the-middle attacks.
To prevent DHCP server spoofing, several countermeasures can be implemented:
MAC spoofing
MAC spoofing is a Data Link (Layer 2) attack where an attacker modifies their device's Media Access Control (MAC) address to impersonate a legitimate device on the network. By doing so, the attacker can bypass MAC address filtering and gain unauthorized access to the network. MAC spoofing can be used in conjunction with other types of attacks, such as man-in-the-middle attacks or session hijacking.
Countermeasures against MAC spoofing include:
CAM table overflow
A CAM (Content Addressable Memory) table overflow attack is a type of network attack that targets the switches in a network. Switches use CAM tables to map MAC addresses to the physical ports on the switch. When a device sends data to another device in the network, the switch checks its CAM table to determine the destination port for the data.
In a CAM table overflow attack, an attacker floods the switch with a large number of fake MAC addresses, filling up the CAM table and causing the switch to overflow. Once the CAM table is full, the switch can no longer map MAC addresses to physical ports, which can cause the switch to fail or start forwarding traffic to the wrong ports.
The consequences of a CAM table overflow attack can be severe, as it can cause network outages or enable attackers to intercept or modify network traffic. Additionally, CAM table overflow attacks can be difficult to detect, as they often occur at the physical layer of the network and can bypass traditional security measures, such as firewalls or intrusion detection systems.
Countermeasures to CAM table overflow attacks include:
Overall, protecting against CAM table overflow attacks requires a multi-layered approach that includes both technical and procedural countermeasures, as well as ongoing monitoring and assessment of network security.
The introduction of wireless technology, increases the potential for security problems including unauthorized access to network resources. By adopting best practices and implementing the latest and strongest encryption and authentication protocols, organizations can minimize the risk of breaches in their wireless networks.
References
5.2. An OVerview of Network Security Architecture
In today's world, networks are the backbone of communication, and they are used extensively for transmitting sensitive data across different locations. As a result, network security is a critical aspect of cybersecurity, and organizations need to ensure that their networks are secure from various threats, such as malware, ransomware, and hacking attacks.
5.2.1. Introduction
Network security architecture refers to the design and implementation of security measures that protect the confidentiality, integrity, and availability of data in a networked environment. A network security architecture provides a comprehensive approach to security that encompasses the entire network infrastructure, including hardware, software, and protocols.
A robust network security architecture involves the deployment of various security controls, including firewalls, intrusion detection and prevention systems (IDPS), virtual private networks (VPNs), access control lists (ACLs), network segmentation, and network monitoring. These components work together to provide a multi-layered approach to security that can detect and prevent security breaches.
The importance of network security architecture cannot be overstated. A poorly designed or implemented network security architecture can leave an organization vulnerable to cyber attacks, which can result in data breaches, financial losses, and damage to the organization's reputation. Therefore, it is essential for organizations to develop and maintain a robust network security architecture to protect their critical data assets.
In the following sections of this module, we will explore each component of a network security architecture in detail and provide guidelines for designing and implementing a comprehensive network security architecture.
Network Security Architecture Components
A comprehensive network security architecture involves the deployment of various security components to provide a multi-layered approach to security. Commonly used components in network security architecture are shown in the table below:
| Component | Description |
|---|---|
| Firewalls | Devices that monitor and control incoming and outgoing network traffic based on a set of predefined security rules |
| IDPS | Devices that monitor network traffic for signs of malicious activity and can automatically block or alert security teams about potential threats |
| VPNs | Provide secure and encrypted communication between different locations over the internet |
| ACLs | Used to control access to network resources by specifying rules |
| Network Segmentation | Involves dividing a network into smaller subnetworks or segments, each with its own security controls and policies |
| Network Assessment | Involves evaluating the security of a network by identifying vulnerabilities and weaknesses that could be exploited by attackers |
| Network Monitoring | Involves the continuous monitoring of network traffic for signs of malicious activity or other anomalies |
Table 5.1: Network Security Architecture Components
Threat modeling
Threat modeling is a structured approach to identifying and evaluating potential security threats and vulnerabilities to a system, application, or network. The process involves analyzing the system, identifying the assets that need to be protected, identifying potential threats and attack vectors, and evaluating the likelihood and impact of each threat. This helps security professionals to identify areas of weakness and develop appropriate mitigation strategies to minimize the risk of a successful attack. Threat modeling is an important part of the overall security architecture process and helps to ensure that security risks are identified and addressed early in the design and development phases of a project.
The results of a threat modeling exercise can be used to inform the selection and design of security controls, such as firewalls, IDPS, VPNs, and other security mechanisms. For example, the results of a threat modeling exercise may indicate that a particular system or application is vulnerable to SQL injection attacks. In response, security architects may choose to implement a web application firewall (WAF) to detect and prevent these types of attacks. Similarly, the results of a threat modeling exercise may indicate that a particular network is vulnerable to unauthorized access, in which case architects may choose to implement a VPN to encrypt network traffic and ensure secure remote access.
5.2.2. Firewalls
Firewalls are network security devices that monitor and control incoming and outgoing network traffic based on a set of predefined security rules. Firewalls can be implemented at the network perimeter, between different network segments, or on individual devices. Firewalls can be hardware-based or software-based and can use various techniques such as packet filtering, stateful inspection, and deep packet inspection to identify and block malicious traffic.
Types of Firewalls
There are several types of firewalls that can be used in network security architecture. The most common types are:
Firewall Best Practices
To ensure that firewalls are effective in protecting the network, the following best practices should be followed:
5.2.3. IDPS
Intrusion Detection and Prevention Systems (IDPS) are security devices that monitor network traffic for signs of malicious activity and can automatically block or alert security teams about potential threats. IDPS can use various techniques such as signature-based detection, anomaly detection, and behavior-based detection to identify and prevent security breaches.
Types of IDPS
There are several types of IDPS that can be used in network security architecture. The most common types are:
IDPS Detection Methods
There are several methods of detection used in IDPS:
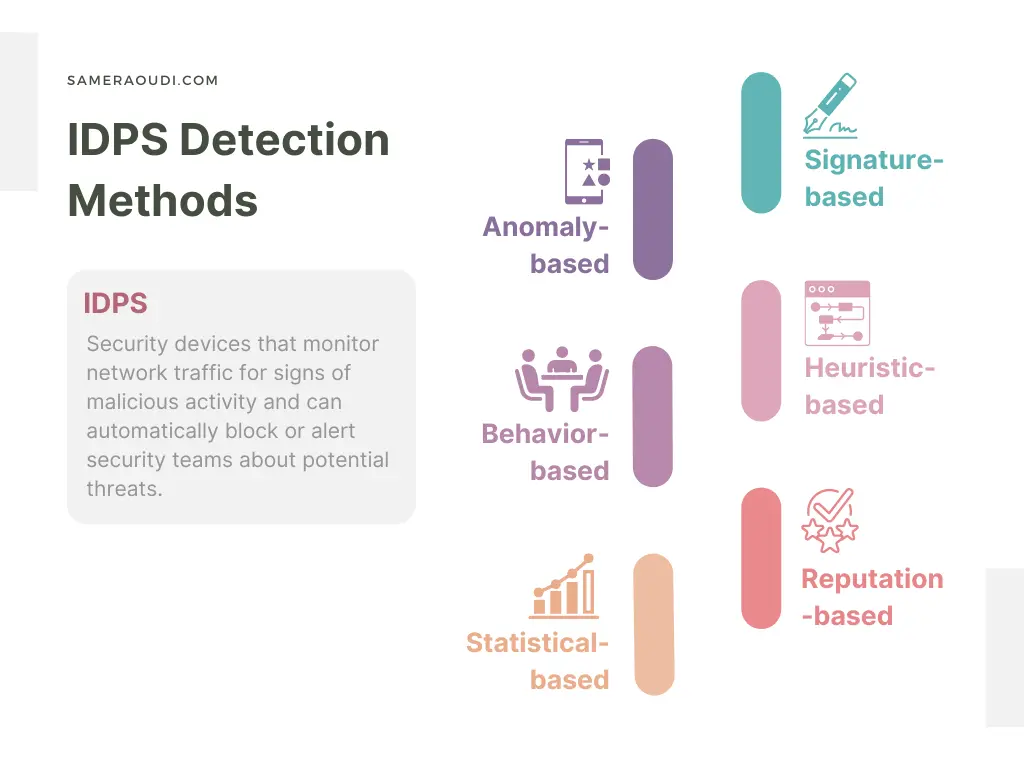
Figure 5.1: IDPS Detection Methods
IDPS Best Practices
To ensure that IDPS are effective in protecting the network, the general best practices outlined in the Firewalls section should be followed, and this includes: Developing an IDPS Policy, Implementing a Defense-in-Depth Strategy, Regularly Monitoring and Updating IDPS Rules, and Regularly Testing IDPS Security. In addition to these general best practices, IDPS should be configured with the appropriate detection method(s) to detect anomalies in network traffic or host behavior.The choice of detection method depends on the specific security needs and risks of the organization.
5.2.4. VPNs
Virtual Private Networks (VPNs) are used to provide secure and encrypted communication between different locations over the internet. VPNs can be used to connect remote workers to corporate networks or to connect different branch offices. VPNs can use various protocols such as IPsec, SSL/TLS, or PPTP to encrypt and authenticate network traffic.
Types of VPNs
There are two main types of VPNs that can be used in network security architecture:
VPN Best Practices
To ensure that VPNs are effective in protecting the network, the following best practices should be followed:
5.2.5. ACLs
Access Control Lists (ACLs) are used to control access to network resources by specifying rules that allow or deny traffic based on a set of criteria such as IP addresses, ports, protocols, or user identities. ACLs can be implemented on routers, switches, or firewalls.
Types of ACLs
There are two types of ACL that can be used in network security architecture:
ACLs Best Practices
To ensure that firewalls are effective in protecting the network, the following best practices should be followed:
5.2.6. Network Segmentation
Network segmentation involves dividing a network into smaller subnetworks or segments, each with its own security controls and policies. Network segmentation can help to contain security breaches and limit the scope of attacks. Network segmentation can be implemented using VLANs, firewalls, or routers.
Benefits of Network Segmentation
Some benefits of network segmentation:
Network Segmentation Best Practices
To ensure that Network Segmentation is effective in protecting the network, the following best practices should be followed:
With networks acting as the backbone of communication, organizations need to ensure that their networks are secure from a growing number of threats. Therefore, it is essential for organizations to develop and maintain a robust network security architecture to protect their critical data assets.
References
5.3. the AAA Framework
In the world of computer security, authentication, authorization, and accounting (AAA) framework is a widely used security model that helps to secure access to computer systems and resources. The AAA framework provides a comprehensive approach to access control by identifying and verifying users, determining their level of access privileges, and tracking their activities. Implementing the AAA framework is a critical step in ensuring the security of any networked system, as it helps to prevent unauthorized access, restrict user privileges, and monitor user activities.
Authentication is the process of verifying the identity of a user, device, or process, typically through the use of usernames, passwords, biometrics, or other authentication methods. This ensures that only authorized individuals or entities are granted access to a particular resource or system.
Authorization refers to the process of granting or denying access to resources based on the authenticated identity and associated privileges or permissions. It ensures that users are only able to access the resources that they are authorized to access.
Accounting involves the tracking and monitoring of user activities and resource usage. This is typically done through the use of logs or other auditing mechanisms, which can be used to track and analyze user behavior and system activity.
The AAA security framework offers several benefits, including:
5.3.1. Implementing the AAA Framework
Implementing the AAA framework requires careful planning and considerations to ensure that it is effective and appropriate for the specific system and network environment. The AAA security framework can be implemented using a variety of technologies and techniques, depending on the specific requirements of the organization. Common ways that AAA can be implemented include Network Access Control (NAC), Remote Authentication Dial-In User Service (RADIUS), and Lightweight Directory Access Protocol (LDAP).
Core Components of AAA
While authentication, authorization, and accounting represent the functional components of AAA, the framework has the following core components necessary for implementation:
Operation of AAA
The following workflow outlines how the core components interact and operate:
Network security protocols and standards provide meachanisms for accessing, using, and/or managing computer networks along with measures to prevent, detect, and correct network compromises.
References
5.4. Network security assessment and monitoring
Network security assessment and monitoring are critical components of a comprehensive security strategy. They help organizations to identify vulnerabilities and threats, and to implement appropriate controls to protect their network resources from unauthorized access, misuse, or theft. The consequences of a network security breach can be severe, including financial loss, damage to reputation, and legal liability. Therefore, it is crucial to regularly assess and monitor network security to ensure the safety and integrity of data and resources.
Network security assessment involves evaluating the security of a network by identifying vulnerabilities and weaknesses that could be exploited by attackers. The assessment may include penetration testing, vulnerability scanning, and risk assessment, among other techniques. Network security monitoring, on the other hand, involves monitoring network traffic and activities to detect and respond to security incidents. This may include intrusion detection, log analysis, and real-time monitoring of network behavior.
5.4.1. Network Security Assessment
Network security assessment is the process of evaluating the security of a computer network by identifying vulnerabilities and weaknesses that could be exploited by attackers. Network security assessment is essential to ensure that network resources are protected from unauthorized access, misuse, or theft.
Assessment Types
There are different types of network security assessments, including vulnerability assessment, penetration testing, and risk assessment.
Assessment Tools
There are various tools and techniques used in network security assessment, including scanning tools, exploitation tools, and network mapping tools.
5.4.2. Network Security Monitoring
Network security monitoring is the process of monitoring network traffic and activities to detect and respond to security incidents. Network security monitoring is essential to identify potential security breaches and respond quickly to minimize the impact of a security incident.
There are various tools and techniques used in network security monitoring, including:
Network Monitoring Tools
There are several Network Monitoring tools that can be used to monitor network traffic and activities:
Network Monitoring Best Practices
To ensure that Network Monitoring is effective in detecting security incidents and optimizing network performance, the following best practices should be followed:
5.4.3. real-world examples
Network security breaches can have severe consequences, but many of them can be prevented or detected earlier by implementing regular network security assessments and monitoring, implementing basic security controls, and promptly detecting and responding to security incidents. Organizations must prioritize network security to protect their data and systems from potential threats and ensure the integrity and confidentiality of their customer's data.
The following are examples and brief analysis of global breaches:
Target data breach: In 2013, Target experienced a data breach that compromised the personal and financial information of over 40 million customers. The breach was caused by a vulnerability in Target's network that allowed attackers to gain access to customer data. Target could have prevented the breach by implementing regular network security assessments and monitoring to identify and patch vulnerabilities in its network. Additionally, Target failed to detect and respond to the breach promptly, allowing the attackers to continue stealing customer data for several weeks.
Equifax data breach: In 2017, Equifax experienced a data breach that exposed the personal and financial information of over 147 million customers. The breach was caused by a vulnerability in Equifax's network that allowed attackers to gain access to customer data. Equifax could have prevented the breach by implementing regular network security assessments and monitoring to identify and patch vulnerabilities in its network. Additionally, Equifax failed to implement basic security controls, such as encrypting sensitive data and implementing multi-factor authentication, which could have prevented or minimized the impact of the breach.
WannaCry ransomware attack: In 2017, the WannaCry ransomware attack infected over 200,000 computers in 150 countries, causing widespread disruption and financial losses. The attack was caused by a vulnerability in Microsoft Windows that allowed the ransomware to spread quickly through networks. Organizations could have prevented the attack by implementing regular network security assessments and monitoring to identify and patch vulnerabilities in their networks. Additionally, organizations could have implemented basic security controls, such as antivirus software and firewalls, to detect and block the ransomware.
Yahoo data breaches: In 2013 and 2014, Yahoo experienced two separate data breaches that compromised the personal information of over 1 billion user accounts. The breaches were caused by a vulnerability in Yahoo's network that allowed attackers to gain access to user data. Yahoo could have prevented the breaches by implementing regular network security assessments and monitoring to identify and patch vulnerabilities in its network. Additionally, Yahoo failed to implement basic security controls, such as encrypting sensitive data and implementing multi-factor authentication, which could have prevented or minimized the impact of the breaches.
Network security protocols and standards provide meachanisms for accessing, using, and/or managing computer networks along with measures to prevent, detect, and correct network compromises.
References
case studyRobust Network Security Architecture for a Mid-Sized BusinessProblem
A mid-sized business was experiencing frequent network security breaches, resulting in data theft and business disruption. The company had a flat network architecture, and all systems were connected to a single network segment. There were no access control lists or network segmentation in place, and the firewall rules were poorly defined. The company was also lacking an intrusion detection and prevention system, which made it difficult to detect and respond to security incidents.
Solution
To address these issues, the company engaged a team of security architects to design and implement a robust network security architecture. The team started by performing a thorough risk assessment and threat modeling exercise to identify potential vulnerabilities and attack vectors. Based on the results of the assessment, the team recommended the following security controls:
Results
After the implementation of the new network security architecture, the mid-sized business experienced a significant improvement in their security posture. The company saw a decrease in security breaches and incidents, and the IT staff was better equipped to detect and respond to security events. The network performance and availability also improved due to the implementation of network segmentation.
Case Study Questions
Attempt to answer the following questions before revealing the model answers:
This case study highlights the importance of a robust network security architecture and the deployment of various security controls.
Research AssignmentNetwork Security ArchitectureObjective
The objective of this research assignment is to explore the various components of network security architecture, including its design, implementation, and management, and understand the best practices for securing computer networks from potential cyber-attacks.
Tasks
In order to evaluate the effectiveness of NIDS in detecting and responding to APTs, the following methods will be used:
Methodology
Deliverables
The research assignment aims to provide a deeper understanding of the best practices for securing wireless networks and their effectiveness in mitigating security threats. The research will provide insights into the latest trends and technologies in wireless network security and help organizations develop a comprehensive and effective wireless network security strategy.
Ads By Google
Module SummaryModule Revision QuestionsModule Glossary| Term | Definition |
|---|---|
| VLAN | A Virtual Local Area Network (VLAN) is a logical network that is created by grouping together devices on a physical network, even if they are not located in the same physical location |
| NIC | A Network interface card is a computer hardware component that allows a computer to connect to a computer network. |
| DHCP | Dynamic Host Configuration Protocol (DHCP) is a network management protocol used to dynamically assign an IP address to hosts on a network |
| MAC | A Media Access Control (MAC)is a unique identifier assigned to a NIC and represents the physical address of a device |
| CAM | A Content Addressable Memory (CAM) is a type of memory that is used in networking devices, such as switches, to store information about the devices connected to them |
| AAA | The Authentication, Authurization, and Accounting framework is a widely used security model that helps to secure access to computer systems and resources |
| PEP | Policy Enforcement Point is a security component of the AAA framework, that enforces access policies and rules |
| PIP | Policy Information Point is a component of the AAA framework, that provides information about the access policies and rules to the PDP |
| PDP | Policy Decision Point is a component of the AAA framework, that makes access control decisions based on the policies and rules defined by the organization |
| IDS | An intrusion detection system (IDS) monitors network traffic for signs of malicious activity or security policy violations |
| SIEM | A security information and event management (SIEM) system collects and analyzes security-related data from different sources to provide a comprehensive view of network security |
| NBA | Network behavior analysis (NBA) monitors network traffic to detect deviations from normal behavior and identify potential security breaches |