

Network Traffic Analysis
In this practical activity, you will use Wireshark to capture and analyze network traffic.
Why this activity? Analyzing network traffic is an essential skill for pentesting. During a pentest you will be looking for specific traffic that spreads out over a number of inbound and outbound packets. Using this skill, you can discover sensitive information and potential weaknesses in your target network; weaknesses which you may exploit later.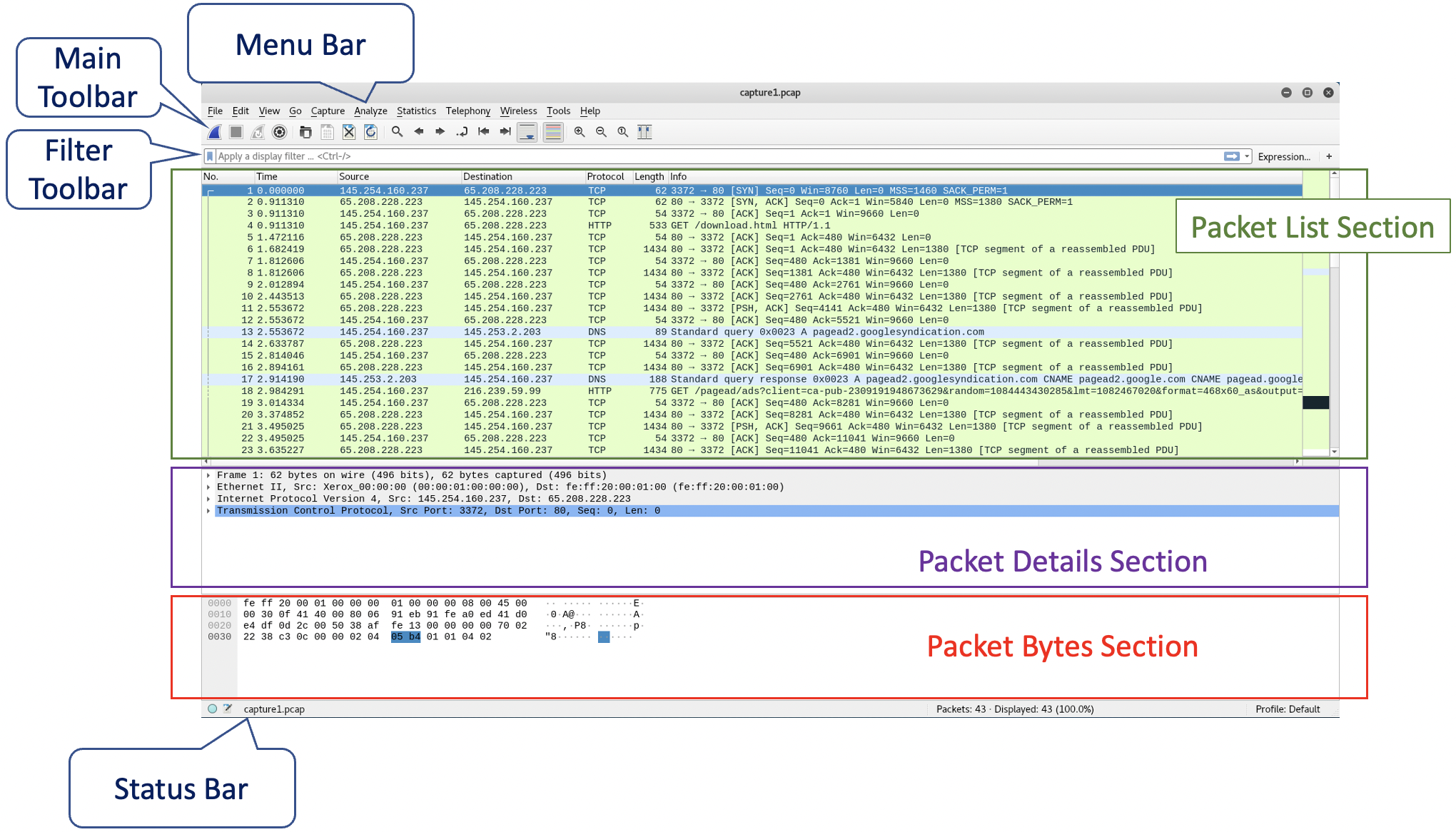
In this activity, you will capture network traffic using Wireshark.
The figure above provides useful information about the Wireshark user interface. Take a moment to locate the different sections.
Don't worry if you cannot locate certain information. Details will follow in the next task
In this activity, you will analyze network traffic.