Social Engineering
In this practical activity, you will use various tools to perform and counter social engineering attacks.
Why this activity? People are the weakest link in the information security chain. Social Engineering is the process of manipulating people to give out sensitive information. After all, the easiest way to get someone's password is to ask for it!In this activity, you will identify Phishing email, examine the signs that expose them, and report them to PhishTank.
Note: To answer related questions, you will need to be able to locate the technical details of a submission
Note: Do NOT visit the website): https://wictziggos.netReport Phishing: To perform the next steps, you will need a phishing email
Note: If registration is disabled, you may skip the reporting steps
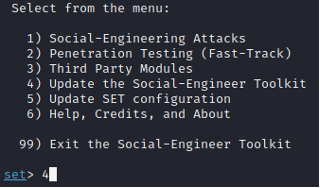
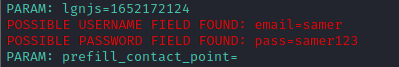
In this activity, you will use The Social Engineering Toolkit (SET) to harvest login credentials from unsuspecting victims