

Network Scanning
In this practical activity, you will utilize different tools to perform network scanning and port scanning as part of vulnerability assessment.
Why this activity? When you are performing Network Penetration Testing, your main objective is to discover active hosts on your target network, and then scan those hosts for vulnerabilities. When vulnerabilities are discovered, you can then attempt to exploit them.In this activity, you will use different techniques and tools to discover active hosts on a network.
In this activity, you will use different techniques to perform port scanning.
In this activity, you will manually search for vulnerabilities and exploits, and perform a quick attack.
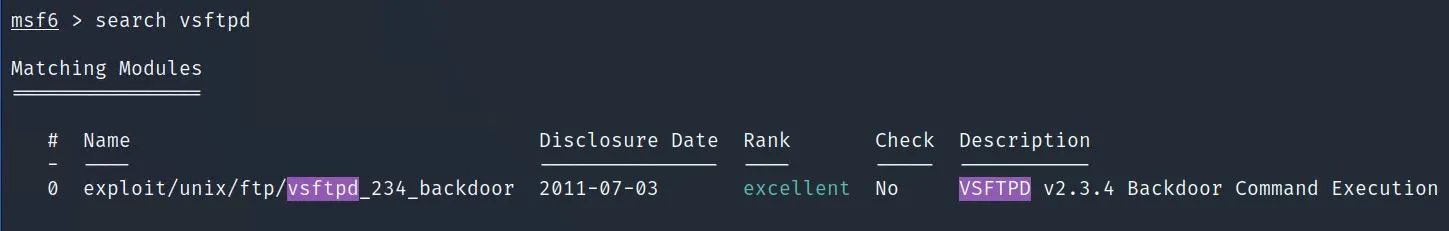
In this activity, you will use a Vulnerability Scanner to discover vulnerabilities.