By completing this task, will be able to improve the security of one of your accounts using passwordless authentication.
Passwordless Authentication is an authentication method that allows a user to gain access to an application, a service or a system without using a password or answering security questions. Instead, the user provides some other form of evidence such as biometric (fingerprint) or a token code.
An Authenticator app is a software-based authenticator that implements passwordless authneticaion and/or 2-factor authentication services, typically using the Time-based One-time Password (OTP) Algorithm. The user would get an OTP that expires
Microsoft Authenticator can be used to sign in to any Microsoft account, or any platform that integrates with with Microsoft Authentication Libraries, without using a password. Microsoft Authenticator uses key-based authentication to enable a user credential that is tied to a device, where the device uses a PIN or biometric (e.g., mobile phone).
Expert Mode
- Choose any of your accounts (e.g., hotmail, gmail, Facebook, instagram, etc.) that supports passwordless or 2FA authentication
- Enable the available authentication method
- Use an Authenticator app (e.g., Microsoft Authenticator or Google Authenticator) to implement passwordless or 2FA authentication
- Test logging in using this new method.
Regular Mode
Show details »
Instal the Authenticator app
- To install the Microsoft Authenticator app on an Android device, scan the QR code below or go to the download page on Google Play
- To install the Microsoft Authenticator app on an iOS device, scan the QR code below or go to the download page on App Store
Enable Passwordless Authentication
- Sign in to any microsoft account you have (e.g., hotmail, outlook, office, etc.), or any acount service that integrates with Microsoft Authenticator
- Go to the "My Profile" section and click Security (may differ from one platform to another)
- Follow the steps provided on the account settings page to enable passwordless, 2FA, MFA, or any alternate authentication feature (the steps and names will differ from one platform to another)
The above step will result in instructions or a QR code that you can use in the next step
Set up the Authenticator app
- Open the Authenticator app and select the (+) in the upper right corner
- Point your camera at the QR code generated in the above step, or follow the instructions provided in your account settings
Test Passwordless Authentication
- Sign out from the account you set up
- Sign is again
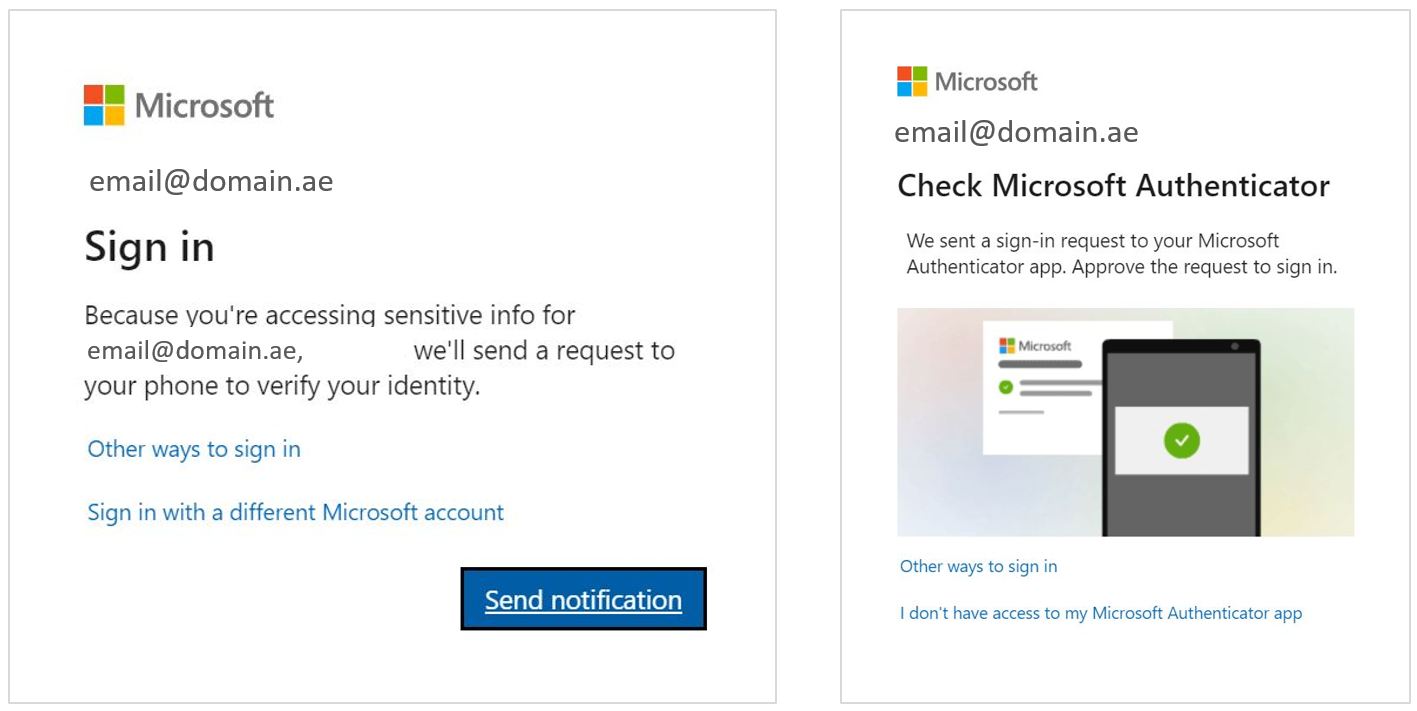
- You will be prompted to to send notification (i.e., to your mobile)
- You will then confirm or reject the signon request
The last two steps may differ based on your account service, but a sample is shown in the screenshot below