

Module 7: Legal and Regulatory ComplianceIntroduction to Information Security Samer Aoudi
Learning OutcomesAn overview of legal and regulatory compliance
The field of information security is constantly evolving, with new technologies, threats, and regulations being introduced all the time. As a result, organizations must have a solid understanding of the legal and regulatory requirements that apply to their operations. This is particularly true in today's increasingly interconnected world, where sensitive information is frequently transmitted and stored electronically.
Legal and regulatory compliance refers to the process of adhering to laws, regulations, standards, and guidelines related to information security and data privacy. In this context, it involves understanding and following the rules and regulations related to the protection of sensitive information and ensuring the privacy of data that is processed, stored, and transmitted by organizations. The goal of legal and regulatory compliance is to minimize the risks of data breaches and other security incidents, and to ensure that organizations are operating in a manner that is consistent with relevant laws and regulations.
Definitions
Before we dig deeper into the topic, let us discuss few important concepts:
Ethics
Ethics refer to the principles, values, and beliefs that govern the behavior of individuals and organizations. Ethics provide a framework for making decisions and determine what is considered to be right or wrong in a given situation.
An example of an ethical principle related to information security is confidentiality. Information security professionals are expected to respect the privacy of sensitive information and to keep confidential information confidential.
Morals
Morals are similar to ethics, but tend to be more personal and subjective. They are the beliefs and values that an individual holds about what is right and wrong.
An example of a moral value related to information security is responsibility. Some individuals believe that it is their moral obligation to protect sensitive information and to act in a responsible manner to minimize the risk of security incidents.
The Law
The law refers to a system of rules and regulations that are enforced by a government or other authority. Laws serve to maintain order and ensure that individuals and organizations act in a manner that is consistent with the greater good.
An example of a law related to information security is the General Data Protection Regulation (GDPR). The GDPR sets out rules for the protection of personal data in the European Union and establishes the rights of individuals with respect to their personal data.
Regulations
Regulations are specific rules and guidelines that are issued by a government or other regulatory body. They are designed to implement and enforce the provisions of laws, and are intended to provide more detailed guidance on how individuals and organizations should behave.
An example of a regulation related to information security is the Payment Card Industry Data Security Standard (PCI DSS). PCI DSS is a set of requirements for organizations that handle credit card information and is designed to ensure the security of cardholder data.
Standards
Standards are guidelines or specifications that are developed by industry organizations or other standards-setting bodies. They provide a common set of requirements for a particular product, service, or process, and are designed to ensure consistent quality and performance.
An example of a standard related to information security is the ISO/IEC 27001 standard for information security management. This standard provides a framework for managing and protecting sensitive information and is widely adopted by organizations around the world.
Policy
A policy is a formal statement of principles, rules, or guidelines that an organization adopts to guide decision-making and behavior. Policies provide a clear and consistent set of expectations for how individuals and organizations should act, and they help to ensure that everyone is working towards the same goals and objectives.
An example of a policy is an acceptable use policy. An acceptable use policy sets out the rules for how employees and other authorized users of an organization's information systems are permitted to use those systems.
Cybercrime
Cybercrime refers to criminal activities that are committed using the internet, computer systems, or other forms of digital technology. Cybercrime can take many forms, including hacking, identity theft, cyberstalking, cyberbullying, and the distribution of malware or other malicious software.
An example of cybercrime is the theft of sensitive information through hacking. In this scenario, a cybercriminal gains unauthorized access to an organization's computer systems or a individual's personal computer and steals sensitive information such as credit card numbers, Social Security numbers, or other personal information. The stolen information is then used for fraudulent purposes, such as identity theft or credit card fraud. This type of cybercrime can have serious consequences for both individuals and organizations, as it can result in financial losses, reputational damage, and loss of privacy.
Understanding LawTypes of Law
There are several types of law, including:
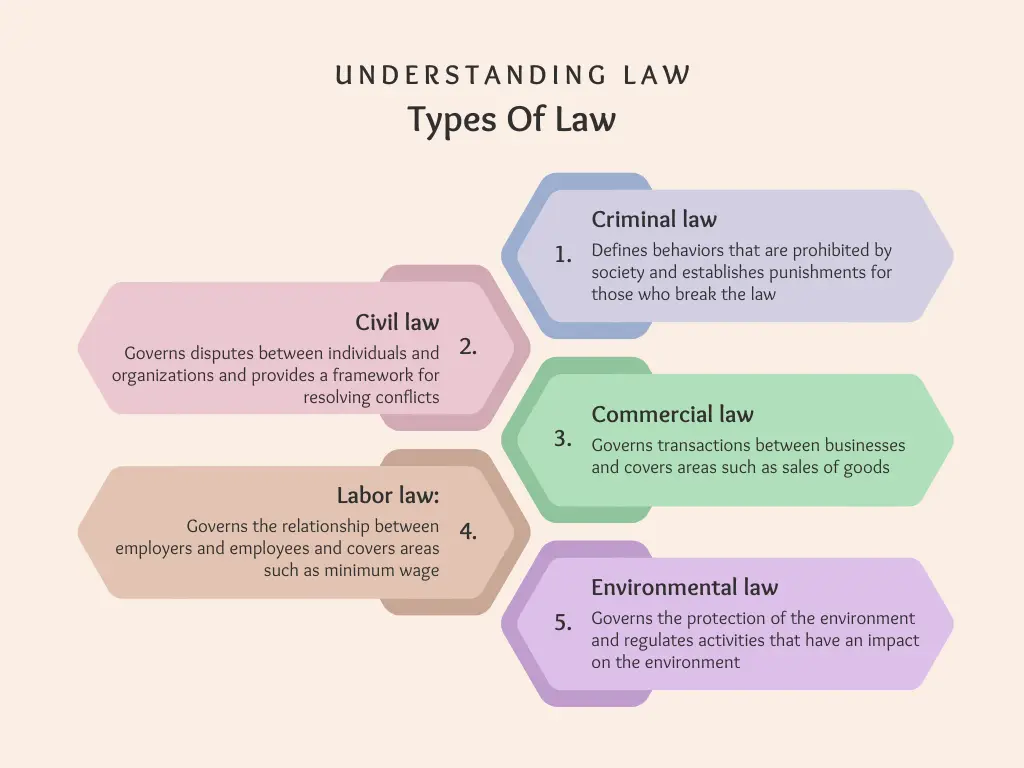
Figure 7.1: Types of Law
Legal Terms
In the context of the law, the following terms are important:
Liability refers to legal responsibility for something, especially for paying debts or for rectifying a wrong. In the context of information security, liability refers to the responsibility of organizations and individuals for ensuring the security of sensitive information and for protecting the privacy of individuals.
Due care refers to the level of caution and attention that a reasonable person should take in similar circumstances. In the context of information security, due care refers to the steps that organizations and individuals should take to protect sensitive information and to prevent data breaches and other security incidents.
Due diligence refers to the level of investigation and care that a reasonable person should take before entering into an agreement or making a decision. In the context of information security, due diligence refers to the steps that organizations should take to assess the security risks associated with new technologies or business partners and to ensure that appropriate security measures are in place.
Scenario: A healthcare organization is storing sensitive medical information of its patients in its computer systems. To fulfill its legal obligation and avoid liability, the organization has a responsibility to take due care and due diligence in protecting this information.
Liability - If a data breach occurs and sensitive medical information is leaked, the healthcare organization may be liable for any damages that result from the breach, such as financial losses, reputational harm, or harm to the privacy of individuals.
Due Care - To fulfill its obligation of due care, the healthcare organization should implement appropriate security measures to protect its computer systems, such as using encryption, regularly updating software and security protocols, and training employees on security best practices.
Due Diligence - To fulfill its obligation of due diligence, the healthcare organization should conduct regular security audits, assess the security of its computer systems and data storage, and ensure that its security measures are up-to-date and appropriate for the level of risk. The organization should also be diligent in its evaluation of third-party vendors and service providers, to ensure that their security practices meet its standards and requirements.
Law vs. Policy
Law and policy are related but distinct concepts that play different roles in shaping the rules and regulations that govern organizations and individuals.
Law is a set of rules and regulations that are created and enforced by a governing authority, such as a government or a regulatory agency. Laws are binding and enforceable, and individuals and organizations can be held legally responsible for violating them.
Policy, on the other hand, is a set of guidelines and principles that are created and enforced by an organization. Policies are not legally binding but are designed to help organizations achieve specific goals or objectives. Policies are generally developed to provide guidance and direction to employees, to ensure that actions and decisions are consistent with the organization's values and goals, and to manage risk.
Intellectual Property
Intellectual Property (IP) refers to creations of the mind, such as inventions, literary and artistic works, symbols, names, images, and designs, for which exclusive rights are recognized and protected by law. IP includes a number of different types of legal rights, including patents for inventions, copyrights for literary and artistic works, trademarks for symbols and logos, and trade secrets for confidential information.
The purpose of IP protection is to encourage innovation and creativity by providing incentives for individuals and organizations to invest time, money, and resources into developing new ideas, products, and processes. IP rights allow creators to control how their creations are used and to receive financial benefits from their exploitation.
In the context of information security, IP protection is an important issue, as digital technology has made it easier to create, distribute, and use IP in ways that can infringe on the rights of the creators. Organizations must take steps to protect their IP and to respect the IP rights of others, such as by implementing secure data storage practices, using digital rights management technologies, and using encryption to protect confidential information. They must also be aware of international IP laws and regulations, as IP rights can vary between countries.
Legal and regulatory compliance refers to adhering to laws, regulations, standards, and guidelines related to the protection of sensitive information and data privacy. It involves understanding and following rules to minimize the risk of data breaches and ensure organizations are operating in accordance with relevant laws and regulations.
References
Data privacy
Personally Identifiable Information (PII) is information that can be used to identify a specific individual. PII typically includes a combination of data elements, such as name, address, social security number, date of birth, or other unique identifying information. PII is considered sensitive and confidential, and its protection is regulated by laws.
What is Data Privacy?
Data privacy refers to the protection of personal information and sensitive data from unauthorized access, use, disclosure, or exploitation. Data privacy is a fundamental right that protects individuals' information and personal data from being collected, used, or disclosed without their consent. It involves creating, implementing, and enforcing policies, procedures, and technologies that protect the confidentiality, integrity, and availability of personal information and sensitive data.
Examples of personal information that need to be protected under data privacy include names, addresses, social security numbers, financial information, and medical records. Data privacy laws, such as the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States, set standards for the collection, use, and storage of personal data, and impose penalties for non-compliance.
Ensuring data privacy is essential for protecting individuals' rights and ensuring the trust of individuals in organizations and governments. It is also important for businesses, as data breaches and loss of sensitive information can result in significant financial losses and reputational damage.
Data Privacy Laws
In this section, we will provide a brief introduction to the key laws and regulations governing data privacy:
GDPR
General Data Protection Regulation (GDPR): The GDPR is a comprehensive data privacy regulation that applies to organizations operating in the European Union. It provides strict standards for the collection, storage, and use of personal data, and gives individuals the right to control their personal information. The GDPR requires organizations to implement appropriate technical and organizational measures to ensure the security of personal data, and to appoint a data protection officer to oversee data privacy compliance.
CCPA
California Consumer Privacy Act (CCPA): The CCPA is a data privacy law that applies to organizations doing business in California. It gives California consumers the right to know what personal information is being collected about them, the right to request that their information be deleted, and the right to opt-out of the sale of their personal information. Organizations must comply with the CCPA's requirements for providing notice, transparency, and consumer control over personal data.
HIPAA
Health Insurance Portability and Accountability Act (HIPAA): HIPAA is a federal law that sets standards for protecting the privacy and security of individuals' health information. It applies to health care providers, health plans, and health care clearinghouses, and requires that they implement appropriate administrative, physical, and technical safeguards to protect the confidentiality, integrity, and availability of health information.
PCI DSS
Payment Card Industry Data Security Standard (PCI DSS): PCI DSS is a set of security standards designed to ensure that all merchants and service providers that accept, process, store, or transmit credit card information maintain a secure environment. Organizations that process credit card transactions must comply with the PCI DSS requirements for protecting cardholder data and preventing payment card fraud.
SOX
Sarbanes-Oxley Act (SOX): SOX is a federal law that requires public companies to establish and maintain effective internal controls over financial reporting. It also requires companies to implement effective information security controls, including access controls, audit trails, and data backup and recovery procedures. SOX applies to public companies and their auditors, and requires them to take steps to ensure the accuracy and integrity of financial information.
data protection and privacy requirements
The requirements for data protection and privacy can vary depending on the specific law or regulation that applies to an organization. However, some of the common requirements are highlighted in the table below:
| Requirements | Description |
|---|---|
| Notice | Organizations must provide clear and concise notice to individuals about the types of personal information being collected, how it will be used, and who it will be shared with. |
| Consent | Organizations must obtain informed consent from individuals for the collection, use, and sharing of their personal information. |
| Data Minimization | Organizations must collect only the personal information that is necessary to fulfill a specific purpose. |
| Data Security | Organizations must implement appropriate technical and organizational measures to protect personal information from unauthorized access, use, disclosure, alteration, or destruction. |
| Data Retention | Organizations must establish policies and procedures for the retention and destruction of personal information. |
| Data Breach Notification | Organizations must have procedures in place for reporting data breaches to the appropriate authorities and for notifying individuals whose personal information has been impacted. |
| Right of Access | Individuals have the right to access their personal information and to know how it is being used. |
| Right to Rectification | Individuals have the right to request that their personal information be corrected if it is inaccurate or out-of-date. |
| Right to Erasure | Individuals have the right to request that their personal information be deleted. |
| Privacy by Design | Organizations must implement privacy protections into their products, services, and processes from the outset. |
Table 7.1: Data Privacy Requirements
Data Privacy refers to the protection of personal information and sensitive data from unauthorized access, use, and exploitation. It requires the creation and enforcement of policies and technologies that protect the confidentiality, integrity, and availability of personal data.
References
Green Computing
The growth of Information and Communication Technology (ICT) has led to the generation of a significant amount of electronic waste and has contributed to a number of environmental issues, including:

Figure 7.2: Green Computing
Green computing is the practice of designing, developing, using, and disposing of computing resources in an environmentally-friendly manner. It involves reducing the environmental impact of computing and using information and communication technologies (ICT) in a sustainable way. This can include reducing the energy consumption of computer systems and networks, using environmentally-friendly materials in the production of computing equipment, and promoting the recycling and disposal of electronic waste in an environmentally-responsible way.
Green computing is becoming increasingly important as the use of ICT continues to grow and as concerns about the environmental impact of computing increase. By adopting green computing practices, organizations and individuals can reduce their carbon footprint and contribute to a more sustainable future for the planet.
Information and Communication Technology (ICT) organizations have several ethical obligations to consider:
green computing laws
There are a number of laws and regulations related to green computing, including the ones shown in the table below:
| Law/Regulation | Description |
|---|---|
| Energy Star | A program run by the U.S. Environmental Protection Agency (EPA) that sets energy efficiency standards for a variety of products, including computers, monitors, and data centers. |
| EU Energy Efficiency Directive | A European Union (EU) directive that sets energy efficiency requirements for a range of products, including ICT equipment, and requires member states to implement measures to promote energy efficiency. |
| Restriction of Hazardous Substances Directive (RoHS) | A European Union (EU) directive that restricts the use of hazardous substances, including lead, cadmium, and mercury, in electronic equipment. |
| Waste Electrical and Electronic Equipment Directive (WEEE) | A European Union (EU) directive that sets requirements for the collection, treatment, and disposal of waste electrical and electronic equipment, including ICT equipment. |
| Electronic Product Environmental Assessment Tool (EPEAT) | A tool that provides a comprehensive rating system for electronic products, including computers and displays, based on their environmental impact. |
Table 7.2: Green Computing Laws
The ICT industry is a major contributor to environmental issues such as waste and pollution. It is both an ethical and legal obligation for the ICT industry to reduce the environmental impact of computing.
References
case studyLaw, Ethics, and Policy in Information SecurityProblem
A large multinational company has experienced a data breach, which has led to the release of sensitive information about its customers. This has resulted in significant damage to the company's reputation and loss of customer trust. The company has now been sued for failing to take adequate measures to protect its customer data, and for not complying with various privacy laws and regulations. The management of the company is now seeking to understand the differences between law, ethics, and policy, and how these concepts play a role in information security.
Solution
To understand the importance of the differences between law, ethics, and policy in information security, the management of the company engaged in a comprehensive study of relevant laws, regulations, and ethical codes related to data privacy and protection. The company also reviewed its existing policies and procedures for data protection and privacy, and identified any areas of improvement. The company then worked with experts in information security, privacy, and ethics, to develop new policies, procedures, and guidelines that would meet or exceed legal requirements, while also aligning with ethical and moral principles.
Results
By understanding the differences between law, ethics, and policy in the context of information security, the company was able to implement effective measures to prevent future data breaches, and to comply with applicable laws, regulations, and ethical codes. This resulted in a significant improvement in the company's information security posture, and helped to restore customer trust and confidence in the company. The company also avoided further legal action, and improved its overall reputation by demonstrating a commitment to privacy and security.
Case Study Questions
Attempt to answer the following questions before revealing the model answers:
This case study highlights the importance of understanding the differences between law, ethics, and policy in information security, and how these concepts can impact a company's ability to protect sensitive information and comply with relevant laws and regulations.
Research AssignmentGreen ComputingIntroduction
The growth of Information and Communication Technology (ICT) has led to a rapid increase in the amount of electronic waste, which is having a severe impact on the environment. Green computing, also known as green IT, is a concept that promotes the design, development, use, and disposal of computer resources in an environmentally sustainable manner. The goal of this assignment is to provide students with the opportunity to understand the concepts of green computing and its importance.
Instructions
Deliverables
Suggested Sources
Assessment Criteria
The assignment aims to educate students on the importance of sustainable computing practices and their impact on the environment.
Ads By Google
Module SummaryModule Revision QuestionsModule Glossary| Term | Definition |
|---|---|
| GDPR | General Data Protection Regulation (GDPR) is a comprehensive data privacy regulation that applies to organizations operating in the European Union |
| CCPA | California Consumer Privacy Act (CCPA) is a data privacy law that applies to organizations doing business in California |
| HIPAA | Health Insurance Portability and Accountability Act (HIPAA) is a federal law that sets standards for protecting the privacy and security of individuals' health information |
| PCI DSS | Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that all merchants and service providers that accept, process, store, or transmit credit card information maintain a secure environment. |
| SOX | Sarbanes-Oxley Act (SOX) is a federal law that requires public companies to establish and maintain effective internal controls over financial reporting |