

Module 3: Network SecurityIntroduction to Information Security Samer Aoudi
Learning OutcomesIntro to Network SecurityNetwork security is a critical aspect of protecting an organization's information systems and assets. With the increasing reliance on technology, networks have become a primary target for cybercriminals and malicious actors. These actors seek to exploit vulnerabilities in networks to gain unauthorized access, steal sensitive information, or disrupt operations. Network security involves implementing a variety of controls, such as firewalls, intrusion detection systems, and encryption, to prevent unauthorized access and protect against a wide range of cyber threats. This chapter will provide an overview of the key concepts and principles of network security, including the types of threats that organizations face, the vulnerabilities that can be exploited, and the controls that can be implemented to protect against these threats.
What is Computer Networking?
A computer network is a collection of interconnected devices, such as computers, servers, printers, and routers, that are connected together to share resources and exchange information. These devices communicate with each other using a variety of protocols and technologies.
Network Protcols
A network protocol is a set of rules and standards that govern the communication between devices in a computer network. It defines how data is transmitted, formatted, and processed between devices, and establishes a common language that allows devices from different manufacturers or operating systems to communicate with each other. Network protocols are responsible for ensuring that data is transmitted reliably and efficiently, and they provide mechanisms for error detection and correction.
The OSI Reference Model
The OSI (Open Systems Interconnection) reference model is a framework for understanding how data is transmitted over a network. It defines a layered architecture that separates the functions of a network into seven different layers, each of which is responsible for a specific set of tasks. The OSI model is a logical model and does not specify any particular protocol, it is used as a reference model to understand the different layers of network protocols and how they work together.
The seven layers of the OSI model are shown in the table below [1]:
| Layer | Function |
|---|---|
| Physical Layer | Responsible for transmitting raw data bits over a physical medium such as a cable |
| Data Link Layer | Responsible for providing reliable communication between devices on the same local network |
| Network Layer | Responsible for routing data packets to their destination |
| Transport Layer | Responsible for ensuring reliable end-to-end communication between devices |
| Session Layer | Responsible for establishing, maintaining, and terminating sessions between applications |
| Presentation Layer | Responsible for translating data into a format that can be understood by the application layer |
| Application Layer | Responsible for providing the interface between the network and the end-user applications. |
Table 3.1: OSI Layers
The OSI model provides a common framework that allows network professionals to understand how different networking technologies and protocols work together to transmit data over a network. It also helps in troubleshooting network issues by identifying and isolating problems at the appropriate layer.
The TCP/IP Stack
TCP/IP (Transmission Control Protocol/Internet Protocol) is a set of networking protocols that are used to transmit data over networks, particularly the internet. It is the foundation of most modern networks, including the internet and most local area networks (LANs). The TCP/IP stack is the combination of several protocols that work together to transmit data over a network.
The TCP/IP stack is made up of four layers shown in the figure below [2]:
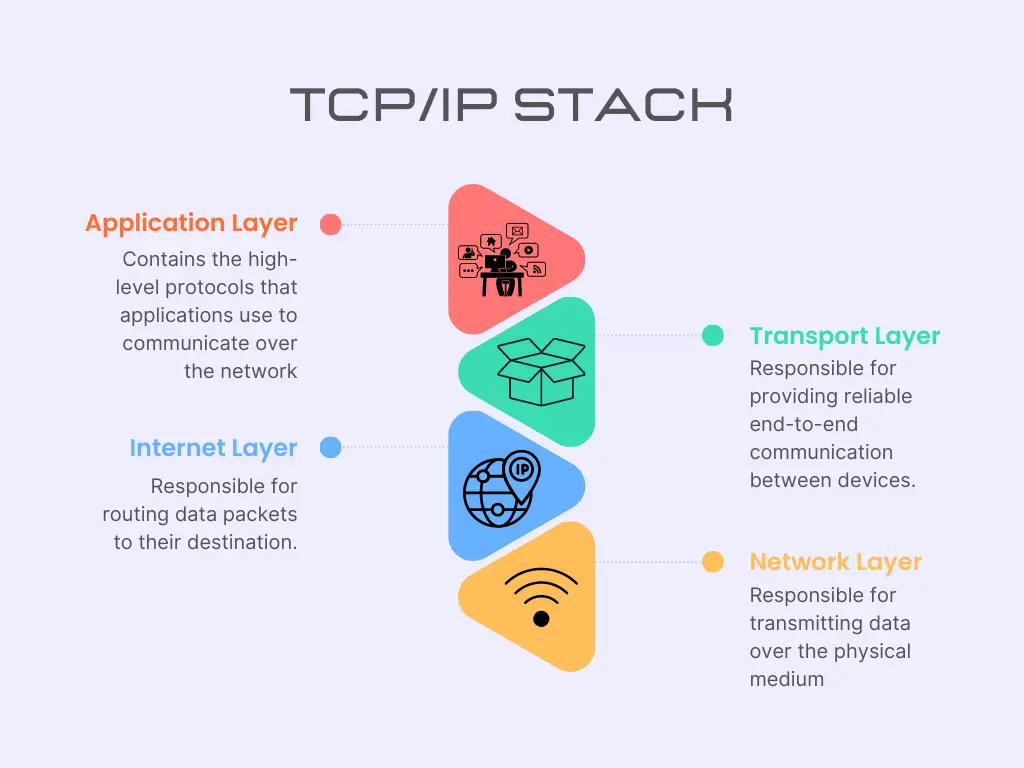
Figure 3.1: TCP/IP Stack Layers
The TCP/IP stack layers and functions are shown in the table below [2]:
| Layer | Function |
|---|---|
| Network Access Layer | Responsible for transmitting data over the physical medium. It includes protocols such as ARP (Address Resolution Protocol) and ICMP (Internet Control Message Protocol) |
| Internet Layer | Responsible for routing data packets to their destination. It includes the IP (Internet Protocol) protocol, which is responsible for addressing and routing packets |
| Transport Layer | Responsible for providing reliable end-to-end communication between devices. It includes the TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) protocols |
| Application Layer | Contains the high-level protocols that applications use to communicate over the network. Examples include HTTP (Hypertext Transfer Protocol), FTP (File Transfer Protocol), and DNS (Domain Name System) |
Table 3.2: TCP/IP Layers
The TCP/IP stack is designed to be a robust and flexible set of protocols that allow different types of devices to communicate with each other regardless of the underlying hardware or software. The protocols in the stack work together to ensure that data is transmitted reliably and efficiently over the network.
The OSI reference model and the TCP/IP stack are both frameworks for understanding how data is transmitted over a network. However, they have some important differences.
The OSI model is a logical model that defines a layered architecture that separates the functions of a network into seven different layers, each of which is responsible for a specific set of tasks. It is a framework for understanding how different networking technologies and protocols work together to transmit data over a network. It does not specify any particular protocol, but it is used as a reference model to understand the different layers of network protocols and how they work together.
The TCP/IP stack, on the other hand, is a set of specific protocols that are used to transmit data over the internet and most local area networks (LANs). It is made up of four layers: the Application, Transport, Internet, and Network Access layers. Each layer has its specific function and protocols to work with.
Simply put, the OSI model is a general model that can be applied to any network communication, while the TCP/IP stack is specifically designed for the internet and most LANs.
TCP/IP Layers and Security
The Application layer of the TCP/IP stack is where most security threats occur, as it is the layer where user interactions and access to data takes place. The following are some common security threats that can occur at the Application layer:
The Transport layer of the TCP/IP stack is responsible for providing reliable end-to-end communication between devices. The main security threats at this layer are:
The Internet layer of the TCP/IP stack is responsible for routing data packets to their destination. The main security threats at this layer are:
The Network Access layer of the TCP/IP stack is responsible for transmitting data over the physical medium. The main security threats at this layer are:
Computer networking is the foundation that enables the communication and exchange of data between different devices and systems. It allows devices to connect and share resources, access the internet, and exchange information. This makes network security an essential aspect of protecting an organization's information and systems.
References
Network Security TechnologiesIntroduction
Network security technologies play a crucial role in protecting networks from a wide range of security threats. These technologies can be used to secure network devices, encrypt data, and monitor network activity to detect and prevent unauthorized access. In this section, we will provide an overview of the most important network security technologies, including firewalls, intrusion detection and prevention systems, VPNs, and encryption. We will explain how these technologies work and their specific use cases to help you understand how to use them to protect your network. Additionally, we will discuss the advantages and disadvantages of each technology, and how to properly implement them for maximum security.
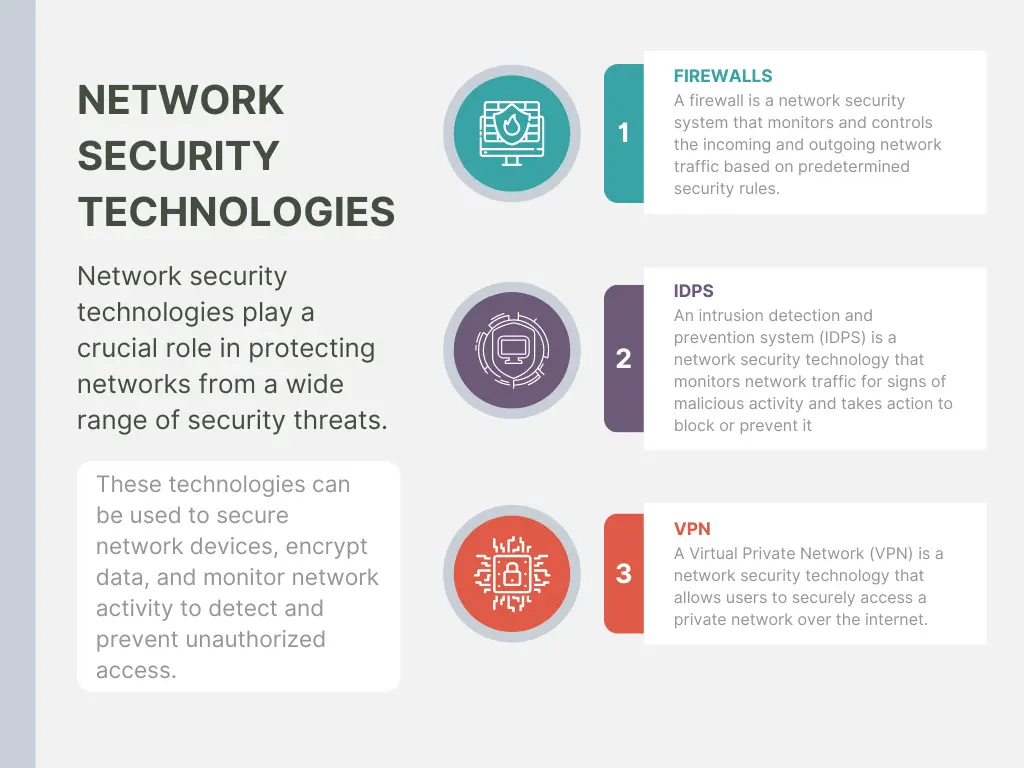
Figure 3.2: Network Security Technologies
Firewalls
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls are typically implemented as a software or hardware solution, and they can be placed at various points in a network to protect it from unauthorized access.
Firewalls use a set of predefined security rules, also called access control lists (ACLs) or policies, to determine which traffic is allowed to pass through and which traffic should be blocked. These rules are based on various parameters such as IP addresses, ports, and protocol. For example, a firewall can be configured to block all incoming traffic from a specific IP address or to only allow traffic over a specific port.
It is important to note that there are several types of firewalls, including:
Firewalls are considered to be an essential component of network security and are widely used to protect both internal and external networks. They are able to block unauthorized access and prevent sensitive data from being stolen or modified. However, firewalls are not a one-stop solution for network security, and it's important to use them in conjunction with other security technologies and best practices for optimal protection.
Intrusion Detection and Prevention Systems (IDPS)
An intrusion detection and prevention system (IDPS) is a network security technology that monitors network traffic for signs of malicious activity and takes action to block or prevent it. IDPS can be implemented as a software or hardware solution, and it can be placed at various points in a network to protect it from unauthorized access.
An IDPS is designed to detect and prevent a wide range of security threats, such as malware, DDoS attacks, and unauthorized access attempts. It does so by analyzing network traffic in real-time, looking for patterns and anomalies that may indicate a security threat. Once a threat has been detected, the IDPS can take action to block the traffic or alert a security administrator.
There are two main types of detection in IDPS:
There are two main types of IDPS: Network Intrusion Detection Systems (NIDS) and Host-based Intrusion Detection Systems (HIDS)
Both NIDS and HIDS have their own advantages, NIDS are better suited to detect network-wide attacks while HIDS are better at detecting targeted attacks on a specific host.
Virtual Private Network (VPN)
A Virtual Private Network (VPN) is a network security technology that allows users to securely access a private network over the internet. VPNs use encryption and authentication to protect the privacy and security of data as it travels over the internet. They are widely used by organizations to protect remote access to their internal networks, and also by individual users to protect their internet browsing activity.
VPNs work by creating a secure and encrypted "tunnel" between the user's device and the VPN server, which enables secure and private communication over the internet. This is achieved by using a combination of protocols and encryption standards, such as Internet Protocol Security (IPsec), Secure Sockets Layer (SSL) and Transport Layer Security (TLS).
VPNs can be used in conjunction with other network security technologies such as firewalls and intrusion detection and prevention systems (IDPS) to protect both internal and external networks. For example, a firewall can be used to block unauthorized access to the internal network, while a VPN can be used to securely allow remote access to the internal network.
Network security technologies such as firewalls, intrusion detection and prevention systems (IDPS), Virtual Private Networks (VPNs) and encryption play a crucial role in protecting networks from various security threats. However, it's important to remember that these technologies are not a one-stop solution for network security and should be used in conjunction with other security technologies and best practices for optimal protection.
Case StudyInvestigating the Effectiveness of Firewalls in Protecting Corporate NetworksBackground
In today's digital age, corporations rely heavily on technology to conduct their business operations. As a result, corporate networks have become a prime target for cyber attacks. One common defense against these attacks is the use of firewalls. Firewalls are designed to block unauthorized access to a network and to protect against malicious activity. However, the effectiveness of firewalls in protecting corporate networks is not well understood.
Case Study
CSF Corporation is a large retail company with a significant online presence. The company's network infrastructure includes a firewall to protect against cyber attacks. In recent months, the company has experienced a number of security breaches, raising concerns about the effectiveness of the firewall in protecting the network.
Methods
In order to investigate the effectiveness of the firewall in protecting the corporate network, the following methods were used:
Results
The network analysis revealed that there were several vulnerabilities in the network infrastructure that could have allowed the security breaches to occur. The firewall configuration review found that the firewall was not properly configured and that several important security measures were not in place. The penetration testing revealed that the firewall was not able to block all unauthorized access to the network. The log analysis showed that there were several attempts to bypass the firewall.
Conclusion
The results of this case study indicate that the firewall was not effective in protecting the corporate network of XYZ Corporation. The vulnerabilities in the network infrastructure, improper firewall configuration, and the ability of attackers to bypass the firewall all contributed to the security breaches experienced by the company. Based on these findings, it is recommended that XYZ Corporation takes steps to address these issues and to improve the overall security of their network. This may include implementing more robust security measures, regular security assessments, and employee security training.
Case Study Questions
Attempt to answer the following questions before revealing the model answers:
This case study highlights the importance of regularly assessing and maintaining network security measures, such as firewalls. It also illustrates the complexity of securing corporate networks and the need for organizations to take a comprehensive approach to security. The findings of this case study can serve as a valuable lesson for other organizations looking to improve their network security and protect against cyber attacks.
Research AssignmentInvestigating the Effectiveness of Network Intrusion Detection Systems in Detecting and Responding to Advanced Persistent ThreatsObjective
The goal of this research project is to evaluate the effectiveness of network intrusion detection systems (NIDS) in detecting and responding to advanced persistent threats (APTs).
Background
With the increasing reliance on technology and the internet in various industries, the threat of cyber attacks has become a major concern for organizations. Advanced persistent threats (APTs) are a particularly significant concern as they are typically carried out by highly skilled and well-funded attackers who are able to evade traditional security measures. One potential defense against APTs is the use of network intrusion detection systems (NIDS), which are designed to detect and respond to malicious activity on a network. However, the effectiveness of NIDS in detecting and responding to APTs is not well understood.
Method
In order to evaluate the effectiveness of NIDS in detecting and responding to APTs, the following methods will be used:
Expected Results
The results of this research project will provide insight into the effectiveness of NIDS in detecting and responding to APTs. It is expected that the results will identify areas where NIDS can be improved to better detect and respond to APTs, as well as areas where additional research is needed.
Assessment Criteria
The results of this research will have important implications for organizations that rely on technology and the internet to conduct their business. By providing a better understanding of the effectiveness of NIDS in detecting and responding to APTs, this research will help organizations to better protect themselves against these types of attacks. Additionally, the results of this research may also inform future developments in the field of network security.
Ads By Google
Module SummaryModule Revision QuestionsModule Glossary| Term | Definition |
|---|---|
| OSI | OSI (Open Systems Interconnection) reference model is a framework for understanding how data is transmitted over a network |
| TCP/IP | TCP/IP (Transmission Control Protocol/Internet Protocol) is a set of networking protocols that are used to transmit data over networks, particularly the internet |
| XSS | Cross-Site Scripting (XSS) is a type of attack that allows an attacker to inject malicious code into a web page, which is then executed by the browser of any user who visits the page |
| IDPS | Intrusion detection and prevention system (IDPS) is a network security technology that monitors network traffic for signs of malicious activity and takes action to block or prevent it. |
| NIDS | Network Intrusion Detection System (NIDS) monitors network traffic for signs of malicious activity and takes action to block or prevent it |
| HIDS | Host-based Intrusion Detection System (HIDS) runs on individual hosts or devices and monitors the system activity and configuration for signs of malicious activity |
| VPN | Virtual Private Network (VPN) is a network security technology that allows users to securely access a private network over the internet |