

Module 8: Risk ManagementIntroduction to Information Security Samer Aoudi
Learning OutcomesAn overview of risk management
Risk, according to NIST [1], is the "net negative impact of the exercise of a vulnerability, considering both the probability and the impact of occurrence." To simplify, risk refers to the potential for loss, harm, or damage that results from uncertainty or exposure to threats. In the context of information security, risk is the likelihood and impact of a security incident that could result in harm to an organization's information assets, such as data breaches, unauthorized access to sensitive information, or system disruptions.
Risks in information security can arise from a variety of sources, including cyber-attacks, human error, natural disasters, and technology failures. Organizations must continually assess the potential risks to their information assets and prioritize their efforts to mitigate these risks.
Risk is typically measured in terms of two factors: the likelihood that a particular risk will occur, and the impact that the risk would have if it did occur. Organizations can then use this information to prioritize their risk mitigation efforts and make informed decisions about the allocation of resources to information security.
Managing Risk
To ensure organizations function effectively and without disruption due to security breaches, we must identify the potential risk and attempt to prevent it, rather than react to an event when it happens. In other words, we need to manage risk.
Risk management in the context of information security refers to the process of identifying, assessing, and prioritizing potential threats and vulnerabilities to an organization's information assets, and implementing measures to mitigate or eliminate these risks. This involves a systematic approach to protecting information systems, networks, and data from unauthorized access, misuse, theft, or destruction.
The goal of information security risk management is to reduce the likelihood and impact of security incidents, and to ensure that the organization is prepared to respond to such incidents effectively. This may involve implementing a range of security controls, such as firewalls, encryption, access controls, and incident response plans.
The Risk Management Process
Assets refer to any valuable component of the organization, including information, systems, networks, and personnel, that need to be protected from unauthorized access, use, disclosure, disruption, modification, or destruction.
Threats refer to any event, action, or circumstance that could potentially cause harm to the assets, such as cyber attacks, natural disasters, and human error.
Vulnerabilities refer to weaknesses in the systems, processes, or practices that can be exploited by threats to cause harm.
At a high-level, the risk management process involves the following:
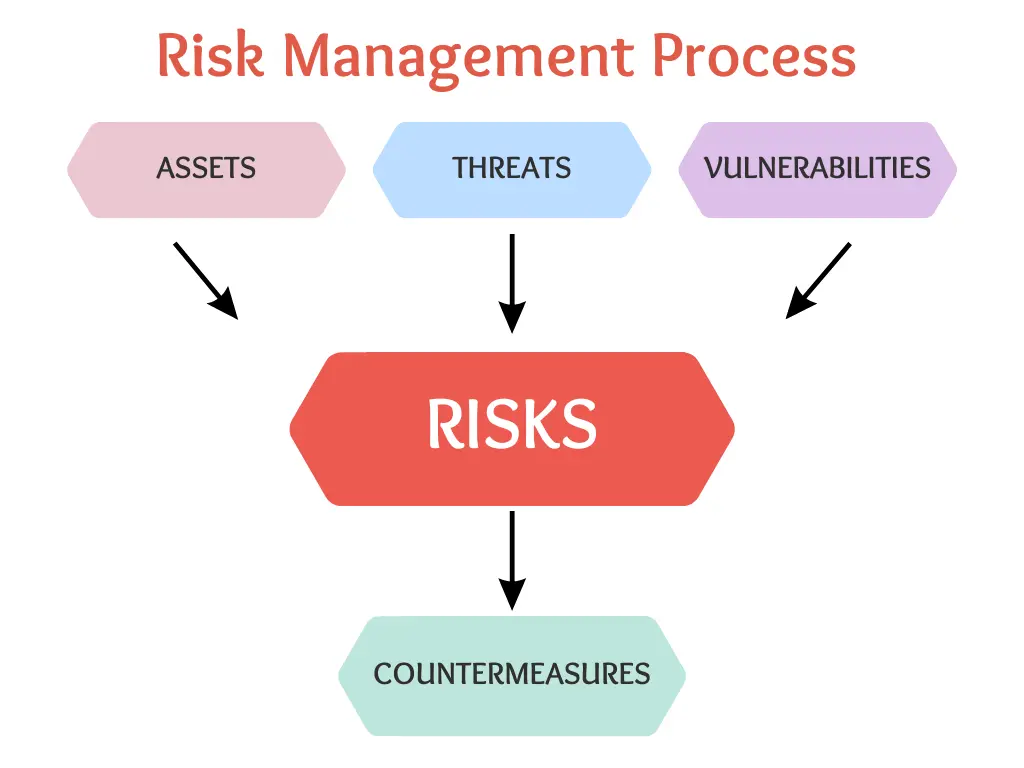
Figure 8.1: Risk Management Process
Countermeasures refer to the treatment or mitigation strategies that are put in place to reduce or eliminate the risks. Countermeasures can include technical solutions, such as firewalls and intrusion detection systems, as well as administrative and physical controls, such as access control policies and physical security measures. The purpose of countermeasures is to reduce the likelihood of a threat occurring and to minimize the impact if a threat does occur.
Risk Management Components
The components of risk management can vary depending on the specific approach or methodology used, but in general, a comprehensive risk management program includes the following components:
1-Risk Identification
Risk identification is the first step in a comprehensive risk management program. It involves identifying the potential risks and threats to an organization's information assets, including both internal and external risks. The goal of risk identification is to identify as many potential risks as possible, so that they can be effectively evaluated and managed.
As a first step, organizations must identify their information assets. By identifying relevant assets, organizations can better understand the information and systems that need to be protected, and can more effectively evaluate the potential risks and threats to these assets. Assets can include a wide range of information and systems, such as the ones shown in the table below:
| Asset Type | Description |
|---|---|
| Data | Including confidential/sensitive information such as personal data, financial data, and trade secrets. |
| IT infrastructure | Servers, network devices, and other hardware and software components that support the organization's operations. |
| Business processes | The processes and systems used to support the organization's operations, such as financial systems, human resource systems, and customer relationship management systems. |
| Reputation | The organization's brand, image, and public perception. |
Table 8.1: Asset Categories
Data classifications are used to categorize data based on its level of sensitivity and the level of protection required. The specific classifications used can vary between organizations, but some common classifications include:
The specific classifications used, as well as the definitions and criteria for each classification, can vary between organizations. It's important for organizations to clearly define their data classifications and ensure that all employees understand and follow the established guidelines.
Classify the following data based on the classifications above:
The process of identifying relevant assets typically involves conducting a comprehensive inventory of the organization's information and systems, and then categorizing these assets based on their level of sensitivity and importance to the organization. A sample inventory can be seen in the table below:
| Asset Name | Asset Type |
|---|---|
| Customer database | Confidential data |
| Employee payroll system | Business processes |
| Web server | IT infrastructure |
| VPN gateway | IT infrastructure |
| Company logo and branding | Reputation |
| Financial reporting system | Business processes |
| Email server | IT infrastructure |
| Trade secrets and proprietary information | Confidential data |
| Employee personal information database | Confidential data |
| Backup and disaster recovery systems | IT infrastructure |
Table 8.2: Sample Asset Inventory
Now that we identified assets, which one(s) do we focus on? In other words, how do we prioritize assets?
Asset prioritization is the process of determining the relative importance of different assets to the organization. This is an important aspect of asset identification because it helps organizations to focus their risk management efforts on the assets that are most critical to the organization and that pose the greatest risk.
The process of asset prioritization involves evaluating the value of each asset to the organization, as well as the potential impact to the organization if the asset is compromised or lost. Assets with a high value to the organization and a high potential impact are considered to be high priority and are given the greatest level of protection. The table below show sample impact matrix which helps in asset prioritization:
| Asset | Type | Data Classification | Impact on Organization |
|---|---|---|---|
| Financial records | Data | Confidential | Significant financial loss, damage to reputation, loss of competitive advantage |
| Employee personal information | Data | Confidential | Legal liability, damage to reputation, loss of trust |
| Trade secrets | Data | Confidential | Significant financial loss, damage to reputation, loss of competitive advantage |
| Marketing plans | Data | Sensitive | Loss of competitive advantage, damage to reputation |
| Server room | Physical asset | N/A | Disruption of operations, data loss, financial loss |
Table 8.3: Sample Impact Matrix
Weighted Factor Analysis (WFA) is one tool that we can use to prioritize assets based on their relative importance or criticality to an organization. WFA works by assigning a weight to each factor that is considered important in the assessment of an asset, and then using these weights to calculate a score for each asset.
Consider the example shown in the tables below:
| Asset | Impact on Sales (50) | Impact on Reputation (25) | Legal Impact (25) | Weighted Score (100) |
|---|---|---|---|---|
| Asset 1 | High (0.5) | Medium (0.5) | High (0.5) | X |
| Asset 2 | Medium (0.3) | High (0.6) | Low (0.25) | X |
| Asset 3 | Low (0.1) | Low (0.25) | High (0.5) | X |
| Asset 4 | Medium (0.3) | Medium (0.5) | Low (0.25) | X |
Table 8.4a: WFA Worksheet (Step 1)
| Asset | Impact on Sales (50) | Impact on Reputation (25) | Legal Impact (25) | Weighted Score (100) |
|---|---|---|---|---|
| Asset 1 | High (25) | Medium (12.5) | High (12.5) | 50 |
| Asset 2 | Medium (15) | High (15) | Low (6.25) | 36.25 |
| Asset 3 | Low (5) | Low (6.25) | High (12.5) | 23.75 |
| Asset 4 | Medium (15) | Medium (12.5) | Low (6.25) | 33.75 |
Table 8.4b: WFA Worksheet (Step 2)
2-Risk Assessment
Risk assessment is the process of evaluating the likelihood and potential impact of specific threats to an organization's assets. It involves analyzing the assets and the threats that they face, and determining the risk level associated with each. This information is then used to prioritize risk mitigation activities and make informed decisions about how to allocate resources.
The objective of risk assessment is to provide a clear understanding of the current security posture of an organization and the threats that it faces. It helps organizations determine the risk that their assets face, including the likelihood of a threat occurring and the potential impact it could have. The results of risk assessment are used to inform decisions about risk mitigation, including resource allocation and prioritization.
Risk assessment is typically performed using a combination of quantitative and qualitative methods, including vulnerability scans, penetration testing, threat modeling, and interviews with subject matter experts. The results of these assessments are then combined to produce a comprehensive view of the risks faced by an organization.
In order to be effective, risk assessments must be conducted on a regular basis and be updated to reflect changes in the organization's environment and assets. This helps organizations stay ahead of potential threats and continuously improve their security posture.
Threats to information security can be categorized in different ways, but the groups shown in the table below are common:
| Category | Description |
|---|---|
| Natural Disasters | Include threats such as earthquakes, hurricanes, and floods, which can cause physical damage to an organization's facilities and disrupt its operations. |
| Technical Failures | Include threats such as hardware failures, software bugs, and network outages, which can cause systems to fail or become unavailable. |
| Human Errors | Include threats such as accidental deletion of data, misconfigured systems, and poor password practices, which are often caused by human mistakes. |
| Malicious Attacks | Include threats such as malware, phishing, and hacking, which are intentionally launched by attackers to harm an organization. |
| Physical Threats | Include threats such as theft, vandalism, and unauthorized access to physical assets, which can result in data breaches and other security incidents. |
| Insider Threats | Include threats such as employees who have authorized access to an organization's systems and data but use that access to cause harm, whether intentionally or unintentionally. |
Table 8.5: Threat Categories
For risk to exist, threats alone are not enough. In many cases, at least one corresponding vulnerability needs to be present. The table below shows specific threats and a possible sample vulnerability:
| Threat | Category | Vulnerability |
|---|---|---|
| Ransomware attack | Malicious Attacks | Unpatched software or lack of backup systems that allow attackers to encrypt and hold an organization's data hostage. |
| Accidental data deletion | Human Error | Lack of data backup and recovery systems, allowing for data to be permanently lost due to human error. |
| Physical theft of laptops or mobile devices | Physical Threats | Lack of physical security measures to prevent the theft of laptops or mobile devices that contain sensitive data. |
| Cyber-espionage | Malicious Attacks | Unsecured systems and networks, or employees who are not trained to detect and report suspicious activity, allowing attackers to gain unauthorized access to sensitive information. |
| Power outage | Natural Disasters | Lack of redundancy in power systems or data backup systems, leading to downtime or data loss in the event of a power outage. |
Table 8.6: Threats & Vulnerabilities
Vulnerability Assessment: One way to discover vulnerabilities in our assets, is by conducting a vulnerability assessment. Vulnerability assessment is the process of identifying and evaluating the vulnerabilities in an organization's information systems, infrastructure, and network. The goal of vulnerability assessment is to identify potential security weaknesses in the systems and to prioritize and mitigate these weaknesses in order to reduce the risk of a security breach.
Vulnerability assessment typically involves the use of automated tools (e.g., Nessus from Tenable) and manual techniques to identify vulnerabilities in the systems, including software, hardware, and network components. This information is then analyzed to determine the likelihood of a vulnerability being exploited, the potential impact if the vulnerability were exploited, and to prioritize mitigation efforts.
Risk is a function of likelihood and impact:
Likelihood is a measure of the probability that a particular threat will occur. It represents the chance or frequency of a specific threat event happening in a given time period. Likelihood is used in risk assessment to determine the probability of an occurrence.
Likelihood is expressed as a numeric value between 0.1 (low) and 1.0 (high), or a percentage between 1% and 100%. When the likelihood is ZERO (0), then, by definition, there is no Risk.
Impact is a measure of the consequences or effects of a threat event on an organization. It represents the extent of damage or harm that would result if the threat were to materialize. Impact can be measured in a variety of ways, including financial losses, disruption to operations, harm to reputation, and loss of sensitive information or intellectual property. In risk assessment, impact is used to determine the overall level of risk posed by a threat to an organization's assets. The impact of a threat is usually expressed as a value on a scale, such as high, medium, or low, or as a numerical score. A high impact indicates a significant potential for harm, while a low impact indicates a minimal potential for harm.
One way to measure impact is using Weighted Factor Analysis (WFA) discussed above.
Risk prioritization is a sub-process of risk identification that deals with determining the order in which risks should be addressed based on their likelihood of occurring and the potential impact they could have on the organization. The goal of risk prioritization is to allocate resources effectively by focusing on the risks that pose the greatest threat to the organization.
In some texts, you might find risk prioritization as a standalone process. As mentioned above, risk is a function of likelihood and impact. The risk equation is shown below:
Risk prioritization helps organizations make informed decisions about where to allocate resources and prioritize risk mitigation efforts. By prioritizing risks, organizations can ensure that they are focusing on the most critical risks and making the most effective use of their resources. This can help organizations reduce the overall risk to their assets and ensure that they are better prepared to respond to potential security threats.
Let us build on the sample data we used before to determine the respective risks:
| Asset | Threat | Vulnerability | Likelihood | Impact | Risk |
|---|---|---|---|---|---|
| Asset 1 | Malware | Outdated software | 60% | 50 | 50 * 60% = 30 |
| Asset 2 | Phishing | Lack of security awareness training | 40% | 36.25 | 36.25 * 40% = 14.5 |
| Asset 3 | Man-in-the-Middle Attack | Unencrypted network communication | 75% | 23.75 | 23.75 * 75% = 17.81 |
| Asset 4 | Ransomware | Lack of backups | 50% | 33.75 | 33.75 * 50% = 16.88 |
Table 8.7: Risk Calculation
Next, we will rank the calculated risks (i.e., prioritize them)
3-Risk Control
Risk Control is the process of developing and implementing strategies to reduce the likelihood or impact of risks, such as implementing security controls, contingency planning, and incident response planning. The goal of risk control is to reduce the overall level of risk faced by an organization, by mitigating or eliminating the sources of risk, or by reducing the impact of security incidents.
There are several strategies that can be used to control risk:
Risk control is an iterative process that involves continuous monitoring and review of risks and risk mitigation measures. This allows organizations to respond to changes in the threat environment, and to ensure that their risk mitigation measures remain effective over time.
Legal and regulatory compliance refers to adhering to laws, regulations, standards, and guidelines related to the protection of sensitive information and data privacy. It involves understanding and following rules to minimize the risk of data breaches and ensure organizations are operating in accordance with relevant laws and regulations.
References
case studyProtecting Confidential Information in a Healthcare OrganizationProblem
A healthcare organization had confidential information stored on their network systems, including patient medical records and financial information. Despite the organization having several security measures in place, such as firewalls and antivirus software, they still encountered numerous data breaches. The breaches resulted in the loss of sensitive information and damage to the organization's reputation, leading to increased regulations and financial losses.
Solution
The organization hired a consultant to conduct a comprehensive risk assessment of their information security system. The assessment revealed that the current security measures were insufficient and that additional controls were necessary to protect confidential information. The consultant recommended implementing a risk management program that included the following steps:
Results
After implementing the risk management program, the healthcare organization experienced a significant reduction in data breaches and a significant improvement in the protection of confidential information. The organization's reputation was restored, and they were able to comply with increased regulations. The organization also saw a reduction in costs associated with data breaches, as well as improved efficiency due to the implementation of more effective security controls.
Case Study Questions
Attempt to answer the following questions before revealing the model answers:
This case study highlights the importance of understanding the differences between law, ethics, and policy in information security, and how these concepts can impact a company's ability to protect sensitive information and comply with relevant laws and regulations.
AssignmentRisk ManagementScenario
Your organization is a medium-sized retail company that operates both online and offline. Your company stores and processes sensitive information of its customers and employees, including names, addresses, phone numbers, emails, and payment information. Your company is looking to improve its information security posture and you have been tasked with conducting a risk identification and assessment process.
Additional information to consider:
Problem
The organization has not conducted a thorough risk identification and assessment process and is concerned about the potential security risks that its information assets may be exposed to.
Solution
You have been tasked with conducting a risk identification and assessment process for the organization's information assets.
Requirements Analysis
Analyze the scenario above and perform the following tasks:
| Asset Name | Asset Type | Data Classification | Impact |
|---|---|---|---|
| Asset 1 | Information | Confidential | Legal liability |
| Asset Name | Asset Type | Data Classification | Impact |
|---|---|---|---|
| Asset 1 | Information | Confidential | Legal liability (50) |
| Asset Name | Threats | Vulnerabilities |
|---|---|---|
| Asset 1 | SQL injection attack | Unpatched software or weak input validation in the application code |
| Asset Name | Threats | Vulnerabilities | Likelihood |
|---|---|---|---|
| Asset 1 | T1: SQL injection attack | V1: Unpatched software or weak input validation in the application code | 50% |
| Asset 1 | T1: ... | V2: ... | 25% |
| Asset Name | Vulnerabilities | Likelihood | Impact | Risk |
|---|---|---|---|---|
| Asset 1 | V1 | 50% | 50 | 25 |
| Asset 1 | V2 | 25% | 50 | 12.5 |
Ads By Google
Module SummaryModule Revision QuestionsModule Glossary| Term | Definition |
|---|---|
| WFA | Weighted Factor Analysis (WFA) is a tool that used to prioritize assets based on their relative importance or criticality to an organization |
| VA | Vulnerability Assessment (VA) is the process of identifying and evaluating the vulnerabilities in an organization's information systems, infrastructure, and network. |
| Likelihood | Likelihood is a measure of the probability that a particular threat will occur |
| Impact | Impact is a measure of the consequences or effects of a threat event on an organization |
| Risk | Risk = Likelihood x Impact |