

Module 9: Implementing SecurityIntroduction to Information Security Samer Aoudi
Learning OutcomesPlanning for & Implementing Security
In today's digital age, the security of sensitive information has become an increasingly critical concern for organizations of all sizes and industries. With the rise of cyber threats such as data breaches, malware attacks, and phishing attempts, implementing robust information security measures has become a top priority for businesses to protect their assets and maintain customer trust. Information security refers to the set of practices, technologies, and policies designed to safeguard the confidentiality, integrity, and availability of information against unauthorized access, use, disclosure, disruption, modification, or destruction. To ensure effective information security, organizations need to adopt a holistic approach that covers not only technical aspects but also human factors and organizational culture. This involves identifying potential risks, defining security objectives, implementing appropriate controls, and regularly monitoring and evaluating the security posture.
Planning for Security
Managing risk, discussed in a previous chapter, is a "complex, multifaceted activity that requires the involvement of the entire organization—from senior leaders/executives providing the strategic vision and top-level goals and objectives for the organization; to mid-level leaders planning, executing, and managing projects; to individuals on the front lines operating the information systems supporting the organization’s missions/business functions." [1]
Organizations plan for information security by following a structured approach that involves several steps. Overall, planning for information security requires a comprehensive and ongoing effort to assess risks, define objectives, develop policies and controls, and continuously monitor and improve security measures.
One element of security planning is contingency planning which includes Incident Response, Disaster Recovery, and Business Continuity plans. The goal of contingency planning is to ensure that an organization can continue to operate in the event of a security incident or disaster. It involves identifying critical systems and data, assessing vulnerabilities, and developing procedures for restoring operations as quickly as possible.
Implementing Security
In order to design and develop controls, organizations often use a high-level approach based called security architecture. Security architecture refers to the design and implementation of security controls and processes to protect an organization's information assets. It is a high-level view of an organization's security requirements, strategies, and structures, which helps to ensure that security measures are aligned with business objectives and risk management needs.
A security architecture may include a range of technical and non-technical controls, such as firewalls, intrusion detection systems, access controls, encryption, authentication, security policies, and incident response plans. These controls are designed to protect information assets from various threats, such as unauthorized access, theft, and data breaches.
Security architecture also takes into account the people, processes, and technology involved in an organization's security measures. It aims to create a security framework that is holistic and integrated, taking into account the interdependencies and interactions between different security controls.
Here are some important security principles that organizations should consider in their information security programs:
Layered Approach
A security program is a set of activities and processes that an organization implements to manage and reduce risk to its information assets. A security program typically includes policies, procedures, and controls to protect the confidentiality, integrity, and availability of information.
A layered approach to security is essential for providing effective protection for an organization's information assets, and organizations should strive to implement controls at each layer to reduce the risk of security incidents and protect against potential threats. There are typically three main layers of information security:
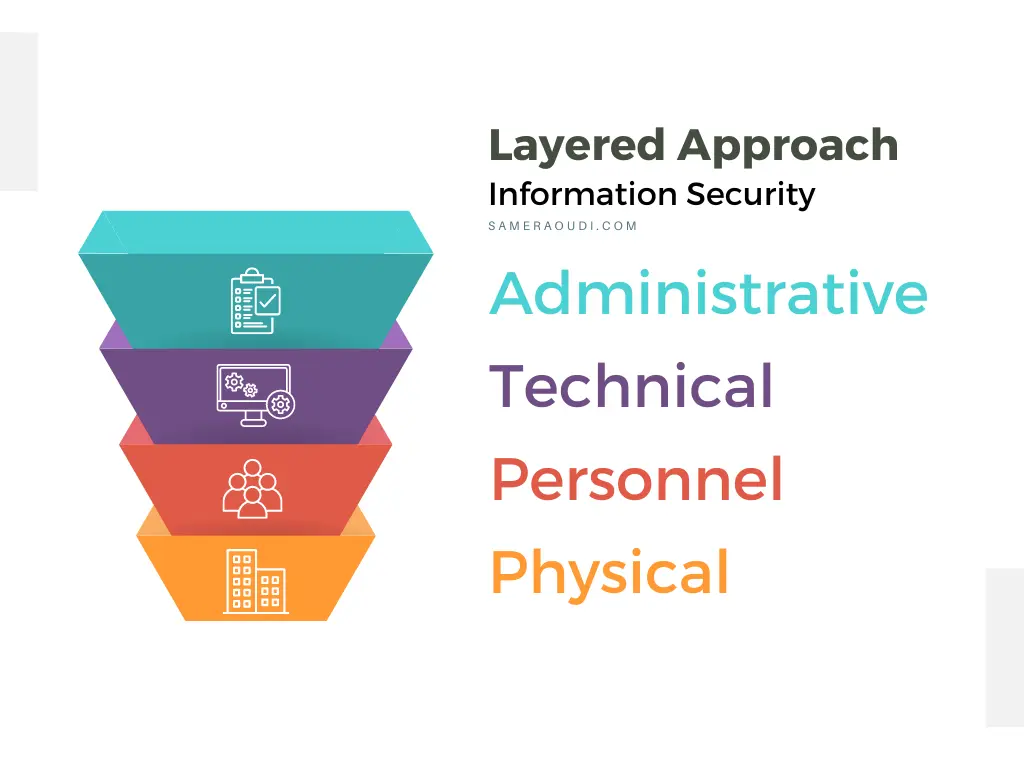
Figure 9.1: Layered Approach to InfoSec
Policy, standards, and procedures (Administrative)
Policy, standards, and procedures are all important components of an organization's information security program, and each plays a distinct role in defining and implementing security controls.
Policy: An information security policy is a high-level statement that defines the overall goals, objectives, and responsibilities of the organization with respect to information security. The policy outlines the organization's stance on security issues and provides guidance for security-related decision making. Policies are typically broad and general, and are intended to provide a framework for more detailed security controls.
Policy Example: An Acceptable Use Policy (AUP) is a policy that defines how employees or authorized users are allowed to use the organization's computer systems and networks. An AUP typically covers topics such as appropriate use of email, internet access, social media, and other information technology resources. The policy would outline the consequences of violating the AUP, which could include disciplinary action or termination of employment.
Standards: Information security standards are more specific and detailed than policies, and provide a set of technical or procedural requirements that must be met in order to comply with the policy. Standards are designed to be measurable and enforceable, and provide a clear set of guidelines for implementing security controls. Standards may address topics such as access control, encryption, incident response, and vulnerability management.
Standard Example: Organizations often create a password standard that defines requirements for the creation, use, and management of passwords. The standard might require that passwords be a minimum length, include a mix of letters, numbers, and symbols, and be changed regularly. The standard might also require that passwords not be written down or shared with others.
Procedures: Information security procedures are even more specific and detailed than standards, and provide step-by-step instructions for carrying out specific security tasks or activities. Procedures are designed to be highly prescriptive and specific, and provide detailed instructions for implementing security controls. Procedures may address topics such as user account management, patch management, or system hardening.
Procedure Example: Relating to the password standard above, an organization can create a password complexity procedure. Passwords must be at least eight characters in length and include a mix of upper and lowercase letters, numbers, and special characters. Passwords should not contain any easily guessable information, such as birth dates or names of family members. Passwords should not be shared with anyone, including coworkers or supervisors.
Key Technology Components (Technical)
The following technology components are essential to providing effective protection to information resources:
Firewall: A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on an organization's previously established security policies. Firewalls act as a barrier between the organization's internal network and the Internet or other external networks.
IDS (Intrusion Detection System): An IDS is a security technology that monitors network traffic for signs of intrusion or malicious activity. An IDS analyzes network traffic and raises an alert if it detects any activity that violates an organization's security policies.
IPS (Intrusion Prevention System): An IPS is a security technology that works in conjunction with an IDS to actively block or prevent malicious traffic from entering the organization's network. IPS devices sit inline with network traffic and can drop, block or alter network traffic to prevent unauthorized access or attacks.
Proxy Server: A proxy server acts as an intermediary between client devices and servers on the internet. Proxy servers can help organizations protect their network by filtering incoming web traffic to prevent access to known malicious or unauthorized websites, and can also help to mask the organization's internal network structure.
DMZ (Demilitarized Zone): A DMZ is a network segment that is separated from the internal network and exposed to the Internet. The DMZ typically hosts publicly accessible servers such as web servers, email servers, and DNS servers. The DMZ is designed to limit the exposure of the internal network to external threats and provide an additional layer of security between internal resources and external threats.
Information Security is an integral part of modern-day organizations. It is both critical and complex, making it an implementation challenge. Adopting a holistic and a structured approach to information security is a key success factor. Successful InfoSec programs often involve the adoption of fundamental security principles as well as a layered approach.
References
Personnel Security
Personnel security is a critical component of information security that focuses on ensuring that employees, contractors, and other personnel who have access to an organization's information and assets are trustworthy and do not pose a security risk. Personnel security includes measures such as background checks, security clearances, and security awareness training to minimize the risk of insider threats, such as unauthorized access, data theft, and sabotage. Effective personnel security programs can help organizations to identify and mitigate potential security risks and protect their information and assets from both internal and external threats.
Employees role in information security
Employees play a critical role in information security as they are often the first line of defense against security threats. Some important roles that employees play in information security include:
Security Education, Training, and Awareness (SETA)
Security education, training, and awareness are critical components of an effective information security program. They aim to educate employees on various aspects of information security and their role in protecting the organization's assets and information from potential security threats. The training can be delivered in various formats, such as online courses, classroom sessions, and workshops [3].
The following are some important topics that may be covered in a security awareness training program:
Hiring and termination practices
The hiring and termination practices of an organization play a critical role in ensuring the security of its information. It is important to conduct thorough background checks and reference checks on all prospective employees to ensure that they have the necessary qualifications, skills, and character to handle sensitive information. When employees are terminated, it is important to have clear policies and procedures in place for revoking their access to systems and data and ensuring the return of all company property.
Background checks and screening processes
Background checks and screening processes are essential for ensuring that employees do not pose a security risk to the organization. These processes can include criminal background checks, credit checks, and employment history checks. It is important to ensure that all checks are conducted in compliance with applicable laws and regulations.
Non-disclosure agreements (NDAs)
Non-disclosure agreements are legal contracts that prohibit employees from disclosing confidential information to unauthorized parties. NDAs can help protect the organization's intellectual property and sensitive information from unauthorized disclosure. It is important to ensure that all employees who have access to confidential information sign an NDA, and that the agreement is regularly reviewed and updated as necessary.
Security threats are not always external, nor are they always intentional. Employees are considered an internal threat and may intentionally or accidently compromise information security. Personnel security focuses on ensuring that employees, contractors, and other personnel who have access to an organization's information and assets are trustworthy and do not pose a security risk.
References
Physical Security
Physical security is an essential component of any comprehensive information security program. It involves the implementation of physical measures to protect the physical assets of an organization, including its buildings, equipment, and personnel, as well as the data and information that are stored and processed within these assets.
Physical security measures are necessary to prevent unauthorized access, theft, damage, or destruction of critical information assets. Examples of physical security measures include access controls, surveillance systems, environmental controls, and perimeter security.
In the context of information security, physical security measures are particularly important because many of the threats to information security, such as theft of laptops or mobile devices, unauthorized access to servers or data centers, and sabotage or destruction of IT infrastructure, require physical access to the assets. Thus, ensuring the physical security of an organization's assets is an important aspect of protecting its information assets and maintaining the integrity, confidentiality, and availability of its data.
Physical security threats
Physical security threats can be broadly defined as any physical force, event, or circumstance that can cause harm, damage, or disruption to an organization's physical assets, personnel, or information systems. The table below shows some examples of potential physical security threats and their associated vulnerabilities:
| Threat | Vulnerability | Example |
|---|---|---|
| Unauthorized access | The lack of appropriate access controls or the failure to enforce access controls effectively | Unauthorized access to physical assets, such as buildings or data centers through tailgating (following an authorized person through a secure access point), lock picking, or bypassing access control mechanisms |
| Theft | Inadequate physical security measures or ineffective tracking or inventory management systems | Theft of employee laptops or mobile phone containing sensitive information |
| Sabotage or vandalism | Inadequate security measures or the failure to identify and address potential threats or vulnerabilities | Cutting fiber optic cables, disabling backup generators, or physically damaging servers |
| Natural disasters | The inability to predict and prevent the natural disaster, as well as the lack of disaster recovery and business continuity plans | Floods, earthquakes, or fires |
| Human error | The lack of employee training and awareness programs | An employee might accidentally leave a laptop containing sensitive information in a public place |
Table 9.1: Physical Threats
countermeasures
There are several countermeasures that organizations can implement to protect against physical security threats. In general, these countermeasures can be grouped into three categories:
Common Countermeasures
Some of the most common countermeasures include [4]:
Deterrents
Deterrents are special measures that are designed to discourage potential attackers or intruders from attempting to breach a facility or gain unauthorized access to sensitive information. Deterrents can include visible security measures such as security cameras, warning signs, security guards, and other physical security measures [5].
Deterrents work by increasing the perceived risk to potential attackers or intruders, making it less likely that they will attempt to breach the facility or access sensitive information. The presence of deterrents can also provide a sense of security to employees and customers, which can help to maintain a positive work environment and protect the reputation of the organization.
However, it's important to note that deterrents alone are not sufficient to provide complete physical security. Deterrents should be used in conjunction with other physical security measures, such as access controls, perimeter security, and surveillance, to provide a comprehensive and layered approach to security.
The figure below shows the application of the Defense-in-Depth principle on physical security:
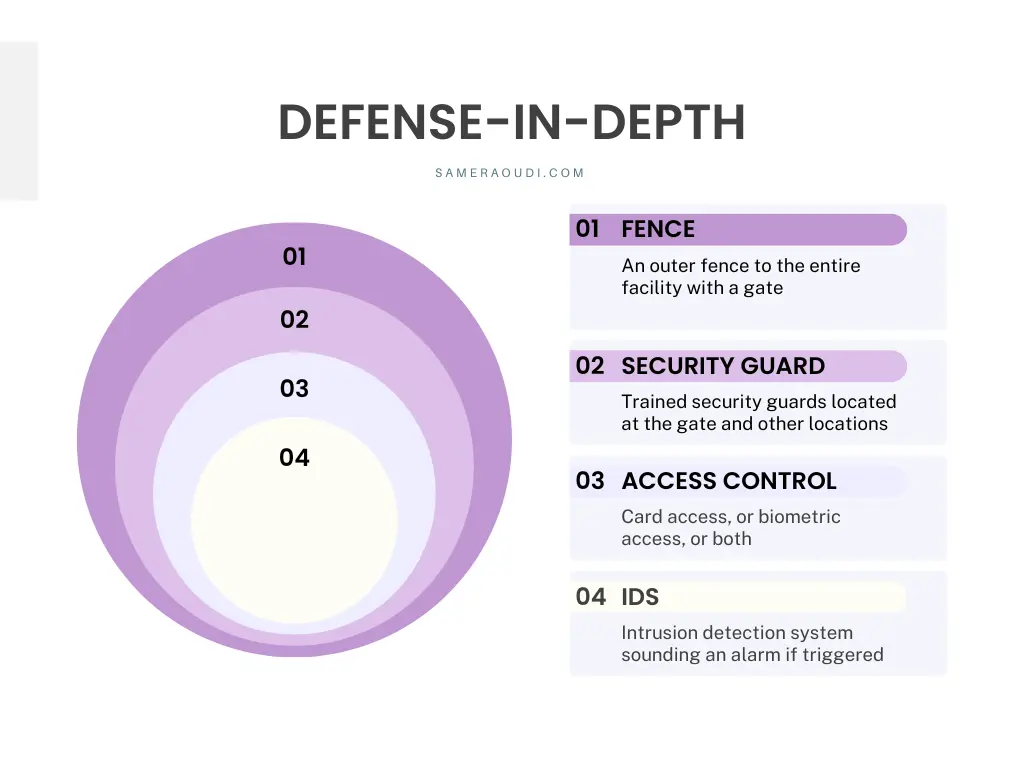
Figure 9.2: Defense-in-Depth
Physical Security Policy
An organization must put in place a Physical Security Policy to protect its physical assets and ensure the safety and security of its employees, customers, and visitors. A well-designed physical security policy addresses the risks and vulnerabilities associated with the physical environment and provides a comprehensive framework for managing and mitigating those risks.
The physical security policy typically covers a wide range of topics, including access control, perimeter security, visitor management, emergency response, incident management, document disposal, and mandatory training. It sets out the rules and procedures for accessing and securing physical assets, such as buildings, equipment, and data storage facilities, and identifies the roles and responsibilities of employees, contractors, and other authorized personnel.
The first layer of security is arguably Physical Security. Physical security is the first line of defense in any comprehensive security program because it provides the foundation for all other security measures.
References
case studyThe Insider ThreatProblem
An organization has identified that an employee has recently started acting suspiciously. This employee has access to sensitive data and the organization is concerned about the potential for an insider threat. The organization is unsure of what steps to take to mitigate the risk.
Solution
To mitigate the potential risk of an insider threat, the organization should implement a personnel security program. This program should include measures to prevent, detect, and respond to insider threats, such as background checks, security awareness training, access controls, monitoring, and incident response procedures.
Results
By implementing a personnel security program, the organization was able to detect and prevent the insider threat. The suspicious employee was identified as a potential threat through their behavior and the organization was able to take appropriate action to mitigate the risk.
Case Study Questions
Attempt to answer the following questions before revealing the model answers:
This case study highlights the importance of understanding the differences between law, ethics, and policy in information security, and how these concepts can impact a company's ability to protect sensitive information and comply with relevant laws and regulations.
Practical AssignmentPhysical Security AssessmentIntroduction
ISO 27001 is a widely recognized international standard that provides a framework for information security management systems (ISMS). The standard specifies a set of guidelines and controls that organizations should follow to ensure the confidentiality, integrity, and availability of their information assets.
Regarding physical security, ISO 27001 specifies a number of guidelines, controls, and other specifics. These include:
Instructions
Report Format
Assessment Criteria
The students will be evaluated on their ability to perform a physical security assessment based on ISO 27001, identify potential vulnerabilities and risks, and provide recommendations for improvement. The evaluation will also take into account the quality of the report and presentation, including the clarity and organization of the material presented.
The assignment provides students with practical hands-on experience in performing a physical security test based on ISO 27001 guidelines. This can be valuable for students who are interested in pursuing careers in information security, as they will likely encounter physical security issues in the workplace.
Ads By Google
Module SummaryModule Revision QuestionsModule Glossary| Term | Definition |
|---|---|
| IDS | IDS (Intrusion Detection System) is a security technology that monitors network traffic for signs of intrusion or malicious activity |
| IPS | IPS (Intrusion Prevention System) is a security technology that works in conjunction with an IDS to actively block or prevent malicious traffic from entering the organization's network |
| DMZ | DMZ (Demilitarized Zone) is a network segment that is separated from the internal network and exposed to the Internet |
| SETA | Security education, training, and awareness are critical components of an effective information security program |
| NDA | Non-disclosure agreements (NDAs) are legal contracts that prohibit employees from disclosing confidential information to unauthorized parties. NDAs can help protect the organization's intellectual property and sensitive information from unauthorized disclosure |