

Module 2: Information Security ThreatsIntroduction to Information Security Samer Aoudi
Learning OutcomesInformation Security ThreatsIn the previous module, we introduced fundamental information security cocepts/terms. Let us recap the ones relevant to this module:
A threat is a potential or actual agent that can cause harm to an organization. This can include various actors such as organized criminal groups, malicious software (e.g. spyware, malware, adware), and even current or former employees who may act against the organization. Additionally, self-propagating malicious software such as worms and viruses can also pose a threat as they can infect and damage systems without the need for human direction.
A vulnerability is a weakness in an organization's environment that a malicious actor could exploit to cause harm. These weaknesses can be found in various areas such as system design, business operations, software, and network configurations, among others.
An exploit is a method or tool used by an attacker to take advantage of a vulnerability in order to cause harm to a target system. Exploits can take many forms, such as code that causes a buffer overflow in software, or a social engineering attack in which an attacker tricks a user into revealing sensitive information.
An attack is an attempt to compromise the security of an information asset. An attack may be successful (breach) or unsuccessful (just an attempt)
The figure below is an illustration that the landscape of cyber threats is always evolving. During the third quarter of 2022, a staggering 15 million data records were exposed worldwide through data breaches. This is a 37% increase compared to the previous quarter and 28% increase compared to the same quarter of 2021 [1]. What is more alarming, however, is the number of attacks attempted in order to breach that many records (the number is in the hundreds of millions).
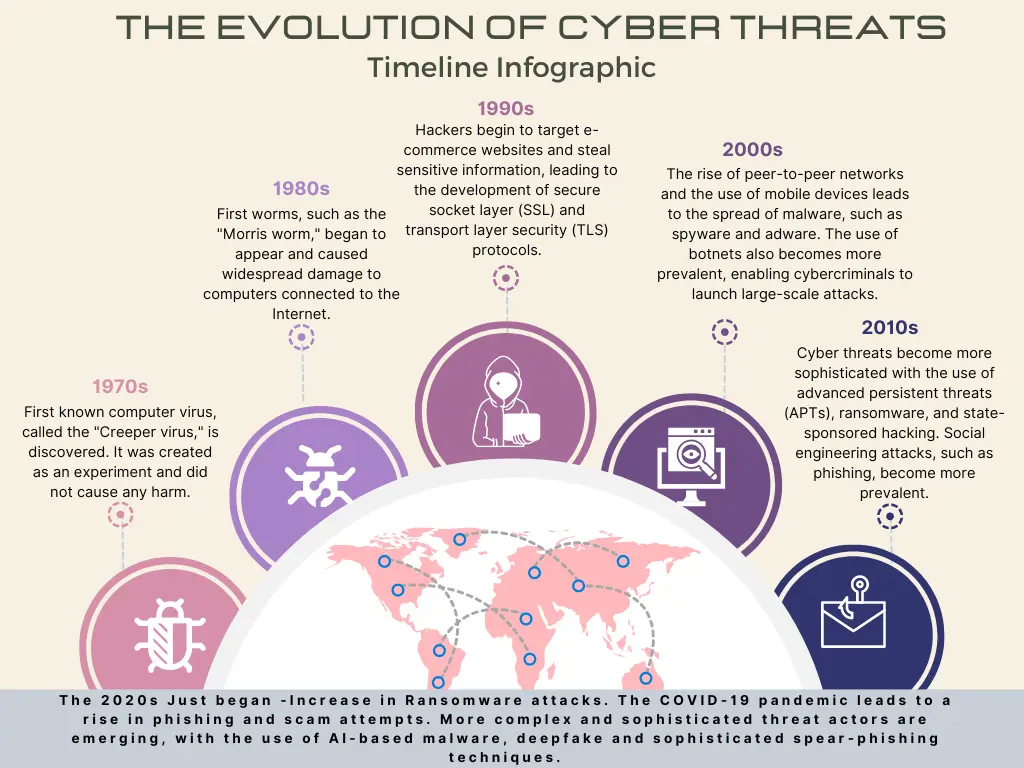
Figure 2.1: Threat Evolution Infographic
Understanding Cyber Attacks
There are different types of attacks that try to exploit existing vulnerabilities in our systems. We may classify attacks based on the method of execution (e.g., physical attacks, social attacks, malware attacks), or based on the proximity (e.g., local vs. remote). CCNA Security defines two braod categories:
The following are common types of attacks:
Malware Attacks
Malware, short for malicious software, refers to any code or program that is written with the intention to harm computer systems or steal, destroy or deny access to information. This category encompasses various types of malicious code such as viruses, worms, Trojan horses, ransomware, active web scripts, and others.
| Malware Category | Description |
|---|---|
| Virus | Virus attaches itself to a file or program. Needs host and human interaction to replicate (e.g. click). |
| Worm | Worm replicates and spreads without a host and without human interaction. |
| Trojan Horse | Trojans disguise themselves as useful programs but include malware. |
| Polymorphic Malware | Malware (virus, worm, etc.) that constantly changes its identifiable feature. Difficult to detect. |
| Backdoor | Malware that allows bypassing normal authentication. |
| Rootkit | Malware that attempts to conceal the existence of malware in the victim host (to avoid detection). |
| Ransomware | Malware that holds computers or files for ransom and blackmails the victim to pay money. |
| Spyware | Malware that collects and sends information from infected computer to attacker. |
| Adware | Displays advertising popups and banners. |
| Logic Bombs | Special malware that activates only when certain conditions are met (e.g. on the 9th of July). |
| Botnet | A collection of interconnected devices infected with malware and controlled by a hacker. |
Table 2.1: Malware Categories
DoS and DDoS Attacks
Denial of Service (DoS) attacks aim to disrupt the availability of information or computer systems by overwhelming them with a high volume of requests. The target system becomes overwhelmed and unable to process legitimate requests, potentially resulting in crashes or slow performance.
A Distributed Denial of Service (DDoS) attack is a variation of DoS where the requests are launched simultaneously from multiple locations. In a mail bombing attack, the attacker sends a large quantity of emails to the target. These types of DDoS attacks are often perpetrated using botnets, a network of compromised devices under the control of an attacker.
Network Attacks
Information is transferred between locations in computer networks via either wired or wireless connections. Attackers may target network traffic (packets of data), in order to gain access or steal information:
Packet sniffing is an attack where a hacker observes and gathers data packets moving through a network.
Spoofing is the process of disguising a communication from the hacker as being from a known, trusted source (e.g., ARP Spoofing)
MiTM (Man-in-The-Middle) attack is when hackers position themselves in the middle of communication between two nodes (e.g. customer and bank), and fool one or both thinking it’s the other.
Social Engineering Attacks
Social Engineering is the art of manipulating people into providing information or a service they otherwise would never have given. Using social skills, an attacker tries to convince people to reveal access credentials (passwords) or other valuable information (e.g., credit card number). Social engineering attacks are successful because they target human characterestics and behavior (e.g., fear, greed, ignorance, etc.). People fall for trickery mainly because of the lack of awareness but sometimes due to their nature (e.g., trusting, greedy).
Phishing attacks, amounting to over 80% of reported security incidents in 2021 [2], is a type of social engineering in which attackers use fake emails, websites, or phone calls to trick people into giving out sensitive information such as passwords or credit card numbers. Attackers often impersonate legitimate organizations such as banks, e-commerce sites, or government agencies to gain the trust of the victim. The goal of phishers is typically to steal the victim's identity or money, or to gain access to their computer or network.
Spear Phishing is a targeted form of phishing that is directed at specific individuals or organizations. Unlike regular phishing, which is usually sent out to a large number of people in the hope that some will fall for the scam, spear phishing attacks are tailored to a specific target. The attackers will often research their victim beforehand, gathering information from social media, company websites, or other sources, in order to make their scam more convincing. Sometimes, attackers target high profile individuals, such as celebrities or politicians, in an attack called Whaling.
Pharming is the process of redirecting legitimate Web traffic (e.g., browser requests) to illegitimate site for the purpose of obtaining private information. This is a technical attack that requires changing hosts file on a victim's computer or exploiting vulnerable DNS servers.
Other Attacks
Misinformation is the act of spreading false, inaccurate, or misleading information, regardless of intent. Disinformation, on the other hand, is knowingly spreading misinformation. Misinformation and disinformation allow for Scams and Hoaxes.
Sabotage or Vandalism are attacks that can range from petty destruction of or damage to information resources, to organized sabotage. For example attackers may deface a web site, which can erode consumer confidence, dropping sales and organization’s net worth.
Spam is unsolicited commercial e-mail that we receive on a daily basis from sources we don’t know. Spam is more a nuisance than an attack, though is emerging as a vector for some attacks.
Theft (Physical or Digital): Physical theft is directly associated with physical security (e.g., stealing a laptop). Digital theft is associated with the digital content and is often more technical and complex (e.g., database breach).
Non-Attack Threats to InfoSec
Although it may seem like, we are not always under attack. Sometimes information is compromised through different threats:
In order to prevent incidents from occuring or to lessen the negative effects of security incidents, organizations must manage security risk.
References
Case Study: Threats to Information SecurityIntroduction
In recent years, the importance of information security has become increasingly apparent as more and more companies and organizations rely on digital technology to store and manage sensitive information. However, as technology advances and new threats emerge, it can be difficult for organizations to keep up and protect themselves from all potential threats. This case study will examine how an organization was able to address multiple threats to its information security.
Background
The organization in question is a large financial institution that deals with sensitive customer information on a daily basis. They had been using traditional security measures such as firewalls and antivirus software to protect their systems, but as technology evolved, they realized they needed to take a more comprehensive approach.
Threats
The organization faced several different threats to their information security, including:
Solution
To address these threats, the organization implemented a number of different security measures, including:
Case Study Questions
This case study demonstrates the importance of taking a comprehensive approach to information security in order to protect against a wide range of threats. By implementing advanced threat detection and response, endpoint security, employee security training, and regular security audits, the organization was able to effectively address the threats it faced and protect its sensitive information. It is important for organizations to keep updated with the latest trends and technology to protect their sensitive information.
Research AssignmentThe Top Cyber Attacks to Prepare for in 2023Introduction
As technology continues to advance, so do the tactics and techniques used by cybercriminals. With each passing year, new and more sophisticated cyber attacks are developed and used to target organizations and individuals. With 2023 on the horizon, it is important to be aware of the potential cyber attacks that organizations should be prepared for [3]. The purpose of this research assignment is to identify and analyze the top cyber attacks that organizations should prepare for in 2023.
To help you get started, read the following blog post: Stay Ahead of the Game: The Top Cyber Attacks to Prepare for in 2023
Instructions
Research Resources
Assessment Criteria
As technology continues to evolve, so do the cyber threats that organizations face. By conducting research on the top cyber threats for 2023, organizations can better prepare for and defend against these threats, ultimately reducing the risk of a successful cyber attack. This research assignment aims to assist organizations in identifying the top cyber attacks to prepare for in 2023 and to provide actionable recommendations for protecting against those attacks.
References
Ads By Google
Module SummaryModule Revision QuestionsModule Glossary| Term | Definition |
|---|---|
| DoS | Denial of Service (DoS) attacks aim to disrupt the availability of information or computer systems by overwhelming them with a high volume of requests |
| DDoS | Distributed Denial of Service (DDoS) attack is a variation of DoS where the requests are launched simultaneously from multiple locations |
| MiTM | MiTM (Man-in-The-Middle) attack is when hackers position themselves in the middle of communication between two nodes (e.g. customer and bank), and fool one or both thinking it’s the other |
| QoS | Quality of Service (QoS): QoS is the overall performance of a network as seen by the users |