

Module 1: Fundamentals of Information SecurityIntroduction to Information Security Samer Aoudi
Learning OutcomesLearning MethodsInformation Security OverviewInformation Security is defined as the "protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide confidentiality, integrity, and availability" [1]. The security of information is essential for people, modern organizations, and governments, as sensitive data and systems are frequently targeted by cybercriminals, hackers, and other malicious actors.
The Personal Computer Revolution in the 1980s marked the rapid growth of the personal computer (PC) industry and this brought about a new type of crime that was not a thing yet, namely computer crime. Meanwhile, the Advanced Research Projects Agency (ARPA) of the US Department of Defense established ARPANET, which evolved into the Internet. The proliferation of the internet and the World Wide Web in the 1990s played a significant role in the popularization of computers. The ability to access information and communicate globally via the internet made computers indispensable tools.
The explosive popularity of the Internet and its Information Superhighway, the WWW, propagated, yet another type of crime that was later dubbed cybercrime. To take it further, recent advancements in Artificial Intelligence (AI) is giving rise to, you guessed it, AI crime.
The Information Age
The partnership between Information and Technology brought about the Information Age, also known as the Digital Age; a period characterized by the rise of information as an invaluable resource and the rapid growth and widespread use of information and communication technologies (ICTs), particularly computers and the internet. This age represents a significant shift from the Industrial Age, which was characterized by manufacturing and physical labor, to an era where information and knowledge have become key drivers of economic, social, and cultural development.
Before computers, information was primarily recorded and managed manually. This included handwritten documents, ledgers, books, and physical files. While relatively safe, Information was localized and often difficult to access unless it was physically stored in a specific location. Retrieving data was time-consuming and the dissemination of information over long distances was slow, relying on postal services or physical delivery methods. Moreover, reproducing and sharing information was labor-intensive, typically requiring handwritten copies or printing using mechanical devices like the printing press.
The advent of computers enabled the conversion of information into digital formats. Data could now be stored, processed, and transmitted electronically. Computers revolutionized information storage and retrieval, making it faster and more efficient. Computers also automated many tasks related to information processing, such as data entry, calculations, and sorting. Moreover, computer networks allowed for remote access to information stored on computers, enabling collaboration and data sharing among users in different locations.
The internet took remote access to a whole new level by providing a global network that connected computers and people worldwide. Information could be accessed from virtually anywhere with an internet connection. Email and other online communication tools allowed for instant exchange of information, transcending geographical boundaries and time zones. Platforms like social media and wikis empowered individuals to create and share their own content, democratizing information production. The internet also transformed commerce and services, allowing for online shopping, banking, education, and entertainment. However, with the increased digitalization and sharing of personal information, concerns about privacy and cybersecurity became prominent issues.
In order to manage and truly leverage information effectively, we need information systems. An Information System (IS) is a collection of hardware, software, data, people, and procedures that work together to provide useful information to an organization. They are used in businesses, government agencies, educational institutions, healthcare organizations, and many other sectors. Organizations must protect all the components of an information system. The components are shown in the figure below:
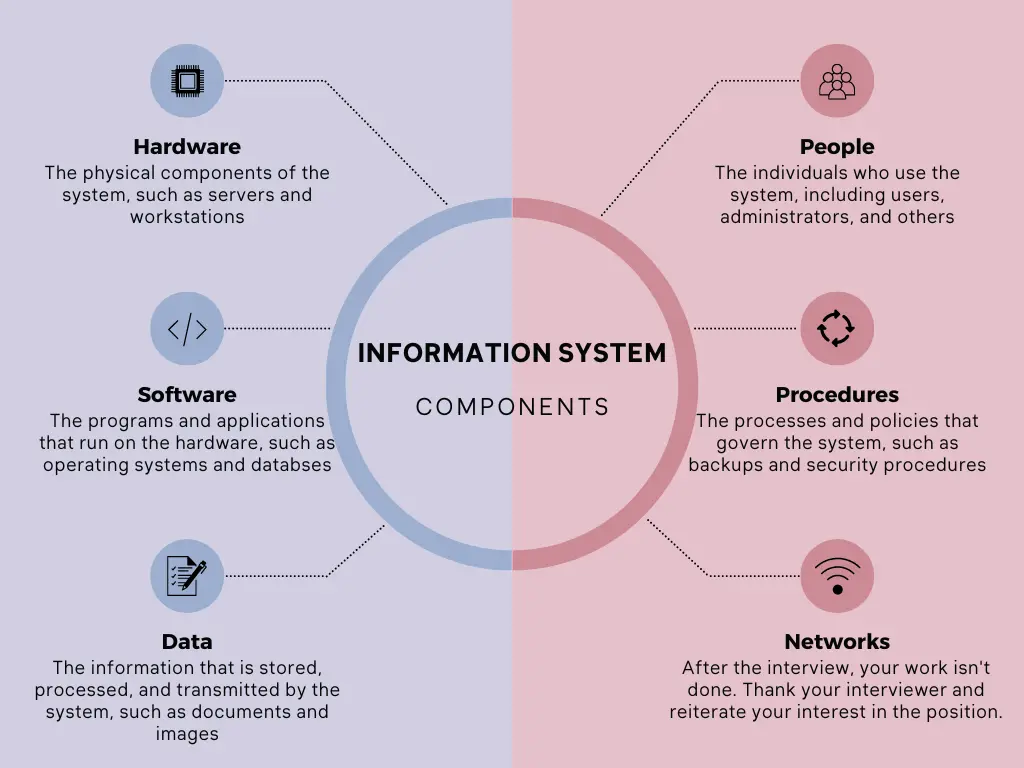
Figure 1.1: IS Components
Why is information security important?
It is imperative that we stress the importance of information today. With the rapid advancements in technology, we are now able to collect, process, and disseminate more information than ever before. The volume of data being generated and shared is staggering and continues to grow at an unprecedented rate. This has led to the creation of a digital economy, where information is one of the most valuable resources available to individuals and organizations.
The rise of the internet, social media and cloud technology, mobile devices and the Internet of Things (IoT) has led to the creation of an interconnected digital landscape where information can be shared, stored and processed globally. This has led to the creation of new business models, new products, and new ways of working. However, with this great potential comes great responsibility. The information that we create and share, has become a target for malicious actors who wish to exploit it for financial gain or to cause harm.
Information security has become a critical concern for both individuals and organizations. Not only do we have a responsibility to protect the sensitive data and systems that we rely on, but we also have a responsibility to protect the personal information of others. Therefore, understanding the principles of information security is essential for anyone in today's digital economy. Those who understand and can apply these principles will be better equipped to protect themselves, their organizations, and others from the various threats that exist in today's digital landscape.
Information security is important because it helps to protect the confidentiality, integrity, and availability (AKA the C.I.A Triad of Information) of sensitive data and systems. Confidentiality refers to the protection of sensitive information from being accessed or disclosed to unauthorized parties. Integrity refers to the protection of information from being modified or corrupted by unauthorized parties. Availability refers to the protection of information and systems from being disrupted or unavailable to authorized parties.
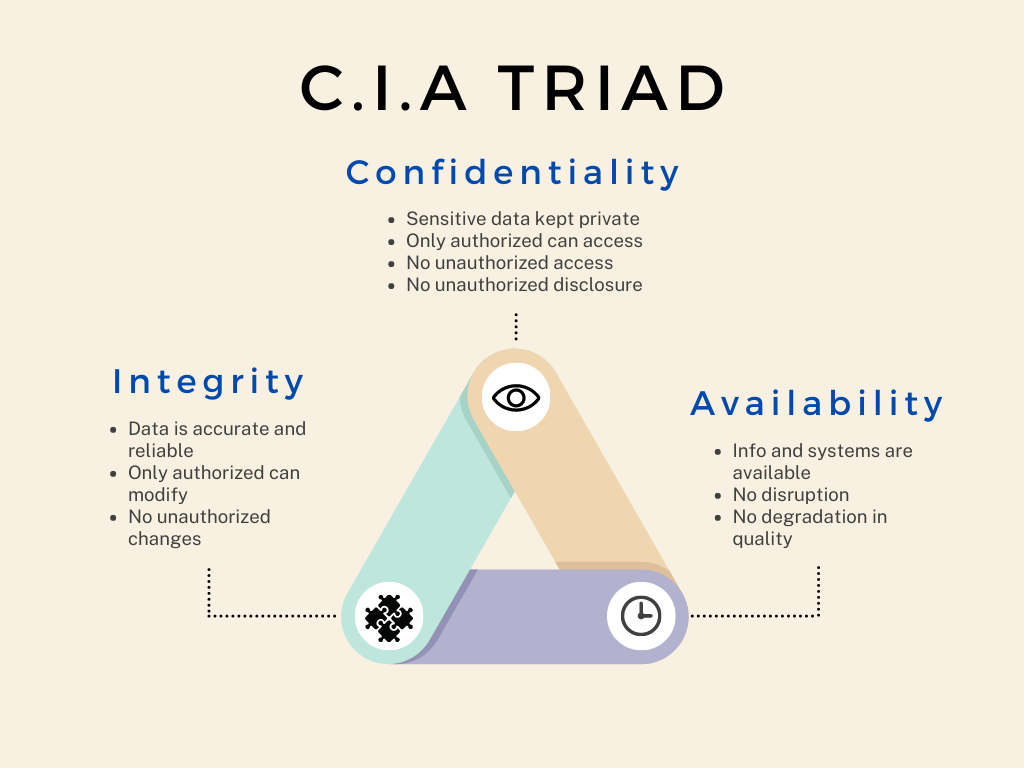
Figure 1.2: C.I.A Triad
In addition to the triad, other critical characteristics of information are relevant from a security viewpoint:
Accuracy: The quality or state of being free from mistake or error and having the value that the end user expects. If information contains a value different from the user’s expectations due to the intentional or unintentional modification of its content, it is no longer accurate.
Authenticity: The quality or state of being genuine or original, rather than a reproduction. Information is authentic when it is the information that was originally created, placed, stored, or transferred.
Utility: The quality or state of having value for some purpose or end. Information has value when it serves a particular purpose. This means that if information is available, but not in a format meaningful to the end user, it is not useful.
Possession: The quality or state of having ownership or control of some object or item. Information is said to be in possession of someone if it is obtained independent of format or other characteristics. While a breach of confidentiality always results in a breach of possession, a breach of possession does not always result in a breach of confidentiality
Data, Information, and Knowledge
We will be using data, information, and knowledge interchangeably in this course, but they have distinct meanings and characteristics.
Data refers to raw facts, figures, and observations. It is the most basic form of information and is often unprocessed or unorganized. For example, a list of customer names and addresses is data. It can be useful, but it doesn't provide much context or meaning.
Information refers to data that has been processed and organized in a way that makes it meaningful and useful. It goes beyond simply describing what happened and provides context and explanations. For example, a report that summarizes customer demographics and buying habits using data on customer names and addresses is information.
Knowledge refers to the understanding and insight gained from information. It goes beyond simply understanding what happened and why, but also encompasses the ability to apply that understanding to make informed decisions and act. For example, a marketing strategy based on the insights and understanding of customer demographics and buying habits from the report on customer names and addresses is knowledge.
Talk the Talk (Important Security Terms)
Information Security. Computer Security. Cybersecurity. Digital Security. Which is it? While people often use these closely related terms interchangeably, it is important to be able to distinguish between them. If security is the state of being protected against threats, the noun before it becomes the object we are trying to protect. In this sense, Digital Security and Computer Security are somewhat limiting. It is more common to use Information Security and Cybersecurity.
Information security focuses on protecting information and information resources. It encompasses a wide range of measures and controls like access control, data encryption, incident response, and disaster recovery. The goal of information security is to protect the confidentiality, integrity, and availability of information and information systems.
Cybersecurity, on the other hand, is the practice of protecting networks, devices, and data from cyber-attacks. It focuses specifically on protecting against unauthorized access or damage to computer systems, mainly through the Internet. It includes technologies, processes, and controls that can be used to protect networks, devices, and data from cyber threats, such as hackers, malware, and other cyber-attacks. It encompasses a wide range of activities, including threat intelligence and penetration testing, to name a few.
Before moving on, I might've mentioned several core security terms that must be defined:
| Term | Definition |
|---|---|
| Risk | Risk in the context of information security, refers to the potential for harm or loss that can occur as a result of unauthorized access, use, disclosure, disruption, modification, or destruction of information or information systems. Risk management is the process of identifying, assessing, and managing these risks in order to minimize the impact of security incidents. |
| Threat | A threat refers to any potential or actual attack against information or information systems. Threats can come from a variety of sources, including hackers, malware, phishing scams, and other types of cyber-attacks. |
| Vulnerability | A vulnerability is a weakness that can lead to undesirable event compromising the system. Examples of vulnerabilities include a weak password, an unpatched application, poor or lack of encryption, and so on. |
| Attack | An attack is an attempt to any unauthorized access, use, disclosure, disruption, modification, or destruction of information or information systems. This could include hacking attempts, malware infections, phishing scams, or other types of cyber-attacks. |
| Exploit | An exploit refers to the use of a known vulnerability in a system, network or device to gain unauthorized access or disrupt the system's operations. This could include malware, scripts, or other tools that are used to take advantage of a vulnerability. Attackers can use exploits to gain access to sensitive information, disrupt services or take control over a system. |
Table 1.1: Cybersecurity Terms
Types of information security
Securing the information of an organization can be a difficult task for many reasons. One factor is that the constantly changing technological environment makes it more difficult to protect against threats. New vulnerabilities and attack vectors are brought about by new technologies, including as the Internet of Things (IoT) and cloud computing. Along with making it harder to keep up with the threat landscape, these technologies also tend to expand the number of endpoints that need to be secured and the volume of data that needs to be protected.
Securing information can be difficult task, as it is a multi-faceted and complex process that involves the integration of technical, administrative, and management controls and the participation of the entire organization. To illustrate this complexity, let us look at different types of information security:
Information security threats
The types and sophistication of threats are constantly changing. Cybercriminals are becoming more organized and motivated, and their techniques and tools are becoming more advanced. This means that organizations must constantly update and adapt their security controls to protect against the latest threats. Organizations face many types of information security risks, such as:
The above is not a comprehensive list of threats to information security. In a rapidly evolving ICT domain, new technologies keep emerging (e.g., Artificial Intelligence, Blockchain, Quantum Computing, and 5G), and with them we can always expect new threats. It is important to note that not all threats are intentional. Human error is an unintentional threat but a threat nonetheless. Natural disasters which can disrupt the operations of entire data centers, for example, are also unintentional but serious threats.
We now know what information security is and why it's crucial for both businesses and people. We discovered that firms need to concentrate on a variety of information security domains, which we dubbed information security types. We also discovered that different threats exist and that their complexity and severity are constantly changing. In summary, information security is a vital but challenging task for contemporary enterprises. The important question is, "What comes next?" The answer is that we must efficiently manage this crucial function. Hence, the need for Information Security Management (ISM).
References
Information Security Management
In general bsuiness context, management is the process of planning, organizing, leading, and controlling the resources of an organization in order to achieve its goals and objectives. Organizations must effectively manage their core business functions (e.g., Operations, Marketing and sales, Accounting and finance, Human resources, and Information Technology). Modern businesses now recognize the need for information security, which can either be a subset of the IT function or, in large organizations, a separate function.
Information security management is a process that organizations use to protect sensitive information and systems from unauthorized access, use, disclosure, disruption, modification, or destruction. It is an essential aspect of modern organizations, as sensitive data and systems are frequently targeted by cybercriminals, hackers, and other malicious actors. This process includes four main steps: planning, implementing and maintaining controls, testing and evaluating controls, and managing incidents.
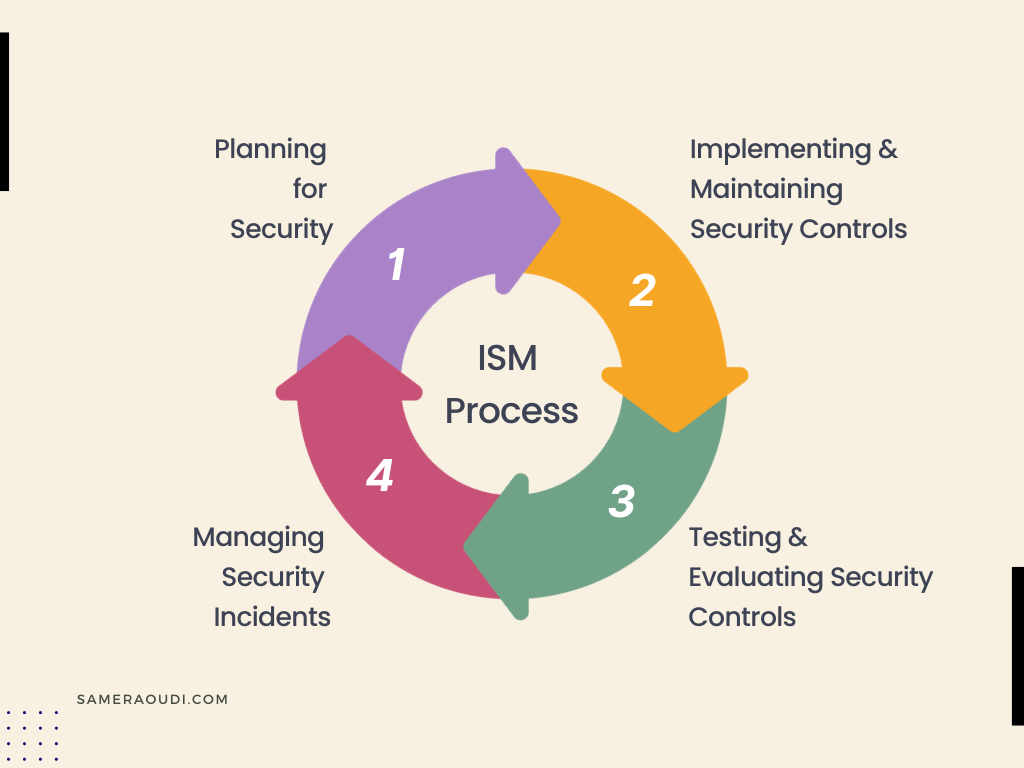
Figure 1.3: ISM Process
Planning for Information Security
If you fail to plan, you are planning to fail -Benjamin Franklin. The first step in information security management is to develop a plan that outlines the goals and objectives for information security, as well as the strategies and tactics that will be used to achieve those goals. This plan should be based on the organization's business needs, as well as the risks and vulnerabilities that the organization faces. The plan should also consider the resources that are available to the organization, including budget, personnel, and technology.
For example, a healthcare organization might have the following goals and objectives for their information security management plan:
Implementing and Maintaining Information Security Controls
Once the information security plan has been developed, the next step is to implement the controls that have been identified as necessary to achieve the organization's information security goals. These controls may include technical measures such as firewalls and intrusion prevention systems, as well as non-technical measures such as employee training and awareness programs. It is important to regularly review and update these controls to ensure that they continue to meet the organization's needs and address emerging threats.
One example of implementing and maintaining information security controls is the use of firewalls. A firewall is a network security device that monitors incoming and outgoing network traffic and allows or denies access to specific network resources based on a set of security rules. Let us examine an example of how a firewall might be implemented and maintained in an organization:
Testing and Evaluating Information Security Controls
To ensure that the organization's information security controls are effective, it is important to regularly test and evaluate them. This can be done through methods such as penetration testing, vulnerability assessments, and security audits. Testing and evaluating information security controls can help to identify weaknesses and vulnerabilities that need to be addressed, as well as confirm that the controls are functioning as intended.
Let us see examples of testing:
Managing Information Security Incidents
Despite the best efforts to prevent them, information security incidents can still occur. It is important for organizations to have a plan in place to respond to and manage these incidents effectively. This plan should include procedures for identifying and containing the incident, eradicating the root cause, recovering from the incident, and performing a post-incident review and analysis. Having a well-developed incident response plan can help to minimize the impact of incidents and prevent them from escalating.
For example:
In order for a incident response plan to be effective, it should be tested and incident response team should be established and trained, and their roles and responsibilities should be clear. Additionally, the incident response plan should be reviewed and updated regularly to reflect changes in the organization's infrastructure, technology, and security landscape.
By having a well-developed incident response plan in place, organizations can minimize the impact of incidents, reduce recovery time and costs, and improve their overall security posture.
Information security management involves planning for and implementing controls to protect sensitive data and systems, testing and evaluating the effectiveness of these controls, and managing information security incidents when they occur. Organizations can use established frameworks to direct their work on information security management. The NIST Cybersecurity Framework, COBIT, and ISO 27001 are a few examples of these frameworks.
Information Security Frameworks
An information security framework is a set of policies, procedures, and guidelines that organizations use to plan, implement, and maintain information security controls. There are several information security frameworks that organizations can choose from, each with its own set of principles, guidelines, and best practices. We will explore some of them shortly; but first, let us examine why organizations need such frameworks:
ISO 27001
One widely-used information security framework is ISO 27001. The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) produced ISO 27001 as a global standard that outlines the requirements for an information security management system (ISMS). The standard is reviewed and updated regularly to ensure that it remains relevant and effective in addressing the latest information security threats and challenges. ISO 27001 covers the following key areas [2]:
NIST Cybersecurity Framework (CSF)
Another popular information security framework is the NIST Cybersecurity Framework (CSF). The CSF is developed and maintained by the National Institute of Standards and Technology (NIST) in the United States. It provides a set of guidelines and best practices for organizations to manage cybersecurity risks [3].
Framework Core
The Framework Core provides a set of activities to achieve specific cybersecurity outcomes.The Core comprises four elements: Functions, Categories, Subcategories, and Informative References. Each function within the core has categories and subcategories. There are 5 functions, 22 categories, and 97 subcategories. Subcategories are outcome-driven statements that can be used to develop a cybersecurity program.
Those pursuing a career in Cybersecurity will find it very useful to understand these core elements. As a starting point, the Core Functions represent high-level cybersecurity activities that you will be doing as a cybersecurity expert. The functions are:
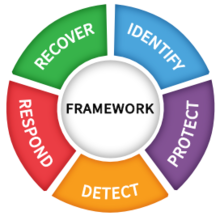
Figure 1.4: NIST Core Functions
The CSF five core functions:
COBIT
COBIT (Control Objectives for Information and related Technology) is another information security framework that is used by organizations to manage information and technology risks. COBIT was developed by ISACA (Information Systems Audit and Control Association). It was first published in 1996.
COBIT provides a comprehensive set of control objectives that cover the following five domains [4]:
Using an information security framework can help organizations to better understand their information security risks and implement appropriate controls to manage those risks. It is important for organizations to periodically review and update their information security frameworks to ensure that they continue to meet the organization's needs and address emerging threats.
References
Ads By Google
Module SummaryModule Revision QuestionsModule Glossary| Term | Definition |
|---|---|
| C.I.A | Confidentiality, Integrity, and Availability are the C.I.A Triad of information |
| APTs | Advanced persistent threats (APTs) are sophisticated cyber-attacks that are launched by well-funded and skilled attackers with a specific target in mind |
| ISM | Information Security Management |
| DMZ | Demilitarized Zone (DMZ) is the area between the internal network and the Internet |
| ISO 27001 | Widely-used information security framework produced by International Organization for Standardization (ISO) |
| NIST | National Institute of Standards and Technology |
| COBIT | COBIT (Control Objectives for Information and related Technology) is another information security framework that is used by organizations to manage information and technology risks |